Enterprise cybersecurity employs coordinated strategies, technologies, and processes to safeguard large organizations against digital threats. Unlike small business security, enterprise cybersecurity tackles the unique challenges of scale — managing vast numbers of employees across dispersed locations, securing complex and interconnected technology environments, and meeting strict regulatory requirements that vary by industry and geography.
Why Enterprise Cybersecurity Matters
The scale and complexity of modern enterprises
Enterprise-level cybersecurity is a different game entirely. Your typical modern enterprise likely operates across networks connecting headquarters, branch offices, remote workers, cloud platforms, and partner systems. You manage thousands of devices, hundreds of applications, and petabytes of sensitive data flowing through on-premises data centers and multiple cloud environments.
Attackers target your organization because it offers high-value rewards. After all, you hold valuable data and can deliver a massive payout. And we aren’t talking just a lone hacker in his mother’s basement; nation-state actors, organized crime groups, and sophisticated hacking collectives invest resources to breach your defenses.
The financial and reputational impact of breaches
IBM’s 2025 Cost of a Data Breach Report shows the average breach costs $4.44 million. Healthcare breaches average $7.42 million per incident, and financial services firms face average costs of $6.08 million.
Beyond immediate losses, breaches also:
- Damage customer trust and shareholder confidence
- Negatively impact stock prices
- Accelerate customer churn
- Invite intensified regulatory scrutiny and audits
Expanded attack surfaces from cloud, remote work, and IoT
As your attack surface expands, your financial stakes grow even higher. Cloud computing has transformed your IT from centralized data centers to distributed architectures that span multiple providers. Remote work extends your corporate networks to home offices and personal devices that lack enterprise-grade security protections. And Internet of Things (IoT) devices, smart building systems, manufacturing sensors, and healthcare monitors proliferate across your environment. Attackers exploit these often overlooked endpoints to establish a foothold, then move toward high-value targets.
Core Components of Enterprise Cybersecurity
Common enterprise cybersecurity threats
When it comes to common enterprise cybersecurity threats, your organization faces four primary threat categories:
- Phishing and social engineering: Attackers send sophisticated emails that impersonate executives, partners, or trusted services to steal credentials, deploy malware, or initiate fraudulent wire transfers. Phone-based attacks may pose as IT support requesting password resets or a vendor updating payment details.
- Ransomware: Attackers spend weeks inside your networks, identifying critical systems and exfiltrating data before encrypting files. They may also combine encryption with threats to publish stolen data, a double extortion tactic that pressures you to pay even when backups exist.
- Insider risks: What happens when the threat is inside the organization? Perimeter defenses can’t stop malicious employees or negligent workers who violate policies.
- Supply chain attacks: You’re only as secure as your weakest vendor. Attackers may compromise trusted vendors or software updates to breach multiple enterprises through a single vulnerability in shared technology.
Enterprise cybersecurity tools and controls
Defending against these threats requires a comprehensive cybersecurity toolkit. For example:
- Firewalls control network traffic by applying a set of predefined rules
- Endpoint protection platforms secure your laptops, servers, and mobile devices
- Identity and access management (IAM) systems ensure that only authorized individuals can reach designated resources
- Security information and event management (SIEM) platforms compile enterprise-wide logs and analyze them to uncover potential security issues
- Cloud security tools protect workloads, data, and configurations in a public cloud environment
The human factor: employee awareness and training
The best technology in the world can’t save your enterprise when employees click malicious links, share passwords, or circumvent security controls for convenience. But teaching them to recognize phishing attempts, handle sensitive data appropriately, and report suspicious activities will help you build a human firewall that strengthens your entire security posture.
Enterprise Cybersecurity Risk Management
Defining enterprise cybersecurity risk management
You can’t eliminate every risk to your enterprise, even trying would bankrupt your organization. Instead, you should allocate security resources based on a threat’s likelihood and potential impact. Enterprise cybersecurity risk management lets you identify, evaluate, and prioritize threats to your organizational assets, allowing you to implement controls that reduce risks to acceptable levels.
Popular frameworks and standards
Several established frameworks can help structure your risk management approach:
- The NIST Cybersecurity Framework provides a flexible approach organized around six core functions: Govern, Identify, Protect, Detect, Respond, and Recover.
- ISO 27001 establishes requirements for information security management systems. Organizations pursue ISO 27001 certification to demonstrate a security commitment to customers and partners, particularly when operating internationally, and to show their dedication to customers and partners.
- CIS Controls offer prescriptive implementation guidance through 18 control categories. You start with basic safeguards before advancing to organizational and supplemental controls.
Your organization may choose to work with multiple frameworks. For example, a mid-sized healthcare provider may begin by mapping assets against NIST CSF’s ‘Identify’ phase, then use CIS Controls 1–5 to secure endpoints and cloud workloads.
Steps in the risk management lifecycle
Your risk management process follows four continuous steps:
- Identify: Catalog hardware, software, data, and intellectual property
- Assess: Combine likelihood and impact to calculate relative priorities
- Mitigate: Reduce risks to acceptable levels by using preventative measures to stop attacks before they happen, detective measures to identify incidents in progress, and corrective measures to limit damage once a breach occurs
- Monitor: Track security metrics, review incidents for patterns, and conduct tabletop exercises and red team assessments
Strategies and Best Practices for Enterprise Cybersecurity
Defense in depth and zero-trust approaches
Modern enterprise security programs are built on two foundational strategies:
- Defense in depth layers multiple security controls so that your entire organization isn’t exposed if one is compromised. Each layer slows attackers and creates detection opportunities.
- Zero-trust architectures don’t trust anyone or anything. They assume every access request is a breach, requiring users and devices to authenticate each time they access applications or data.
Implementation tip: Start by enforcing MFA and network segmentation before rolling out a full zero-trust model.
Governance, compliance, and policies
Strategy means nothing without structure to enforce it.
- Strong governance uses defined roles, responsibilities, and escalation procedures to establish accountability for security decisions.
- Executive representation on your security steering committee will ensure your security and business objectives align and that you have adequate funding.
- Compliance programs address your regulatory obligations like GDPR, CCPA, HIPAA, or PCI DSS.
- Regular assessments identify gaps before regulators do.
Implementation tip: Create a simple RACI matrix (Responsible, Accountable, Consulted, Informed) for your top 10 security decisions before building broader governance structures.
Vendor and third-party risk management
Your security perimeter extends beyond your walls. Vendors and partners who access your enterprise systems expand your attack surface beyond your direct control. But thankfully, there are steps you can take to mitigate risk, including:
- Building security requirements into your procurement processes before data sharing begins
- Evaluating third parties’ security postures through questionnaires, audits, and contract requirements
- Classifying vendors by risk level, requiring high-risk partners to take part in annual assessments while applying lighter reviews to low-risk relationships
Implementation tip: Inventory existing vendors with system access, tier them by risk level, and focus initial security reviews on high-risk partners only.
Regular audits, testing, and continuous improvement
Even the best security programs degrade without regular validation. Internal audits verify that your security controls operate as designed. Vulnerability assessments scan systems for known weaknesses, letting you prioritize patches based on exploitability and asset criticality. Penetration testing simulates real-world attacks to identify gaps. Continuous improvement incorporates lessons from incidents, tests, and audits into updated policies and controls.
Implementation tip: Schedule quarterly vulnerability scans and one annual penetration test, then track remediation with a 30/60/90-day calendar based on severity.
Enterprise Cybersecurity Solutions and Services
Key categories of enterprise security solutions
Your security stack requires solutions across five important areas:
- Endpoint security: Protect laptops, desktops, servers, and mobile devices.
- Network security: Monitor traffic flows, block malicious connections, and segment environments.
- Cloud security: Address infrastructure-as-a-service, platform-as-a-service, and software-as-a-service risks.
- Identity solutions: Centralize authentication, authorization, and privileged access management across on-premises and cloud applications.
- Managed detection and response (MDR): Get 24/7 monitoring, threat hunting, and incident response through services that aggregate security data from multiple sources and apply expert analysis to identify sophisticated threats.
When to consider managed service providers vs in-house security
Consider this: Building in-house security requires a substantial investment in tools, processes, and talent that takes years to mature. Managed security service providers give you immediate access to experienced analysts, established procedures, and threat intelligence. These services convert variable costs into predictable subscriptions.
Certainly, in-house teams can provide a deep understanding of your business’s organizational culture. That’s why many enterprises adopt hybrid models, allowing internal staff to handle strategy and governance while relying on managed service providers to deliver 24/7 monitoring and specialized capabilities.
CTA: Find a managed service provider that’s available when and where you need them. Xantrion offers proven enterprise cybersecurity services across California, including in San Francisco, San Jose, Los Angeles, Sacramento, and San Diego. Learn more about our services.
Services that scale with enterprise needs
The right provider delivers capabilities that grow with your organization. For example, providers like Xantrion combine technology platforms with human expertise to monitor security events around the clock, delivering faster threat identification and containment than most in-house teams can achieve.
Additionally, Xantrion offers:
- Vulnerability management services, conducting regular scans and tracking remediation progress.
- Compliance services that help you navigate regulatory requirements and prepare for audits.
- Incident response services that ensure that when a breach occurs, expert help arrives within moments.
Industry-Specific Enterprise Cybersecurity Needs
Healthcare cybersecurity
Healthcare organizations operate under strict HIPAA compliance regulations, protecting electronic health records, medical device data, and payment information. When breaches occur, they not only expose sensitive patient data but also disrupt care delivery through ransomware attacks that lock critical systems.
Medical devices present a particular challenge for healthcare cybersecurity service providers. Many run outdated operating systems that can’t receive security patches without voiding warranties or requiring costly recertification. Your healthcare organization can address this issue through network segmentation, which isolates medical devices while continuously monitoring for anomalous behavior.
Financial services cybersecurity
Financial services firms operate in a state of constant vigilance, with attackers continually targeting customer accounts, payment systems, and trading platforms. PCI DSS requirements dictate how they handle credit card data, while federal and state regulators mandate comprehensive security programs far beyond basic protections.
Fraud prevention systems work in real-time to analyze transaction patterns and catch suspicious activities before losses mount. Multi-factor authentication enhances account security by adding an additional layer of verification.
Manufacturing and critical infrastructure cybersecurity
Manufacturing and critical infrastructure organizations must protect information technology networks and operational technology that controls physical industrial processes. SCADA systems, programmable logic controllers, and human-machine interfaces keep factories and infrastructure running — but many were designed decades ago without modern security features.
The threats are particularly severe. Nation-state actors actively target energy grids, water systems, and transportation networks, viewing these critical infrastructure assets as strategic resources. Standard IT security tools often fail to work in operational technology environments, where uptime and safety are paramount. Instead, organizations rely on air gaps to isolate systems, unidirectional gateways to control data flow, and specialized monitoring solutions for industrial environments.
Choosing the Right Enterprise Cybersecurity Partner
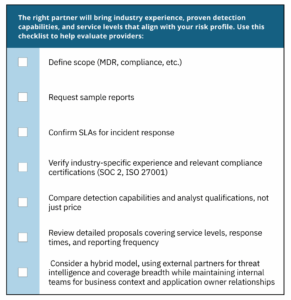
Criteria to evaluate a cybersecurity partner
How do you choose the right cybersecurity partner for your enterprise? First, look for experience. The ideal partner will work with companies of similar size, industry, and regulatory environment. Additionally, ask about compliance certifications showing that the provider meets recognized security standards.
How to compare providers and services effectively
Not all managed security providers deliver the same value, so ensure you carefully evaluate your options before committing. Request detailed proposals that specify their service levels, response times, and reporting frequency. And compare providers based on their detection capabilities and analyst qualifications, rather than just price.
Why enterprises often combine partners with in-house expertise
You don’t have to choose between fully outsourced or fully in-house security. A hybrid security model leverages partners for breadth while maintaining internal teams for depth. External providers bring cross-industry threat intelligence, while internal teams understand business context and maintain relationships with application owners.
FAQs About Enterprise Cybersecurity
What is enterprise cybersecurity in simple terms?
Enterprise cybersecurity protects the digital assets of large organizations through coordinated strategies, tools, and processes that defend against cyber threats.
What are the biggest enterprise cybersecurity threats today?
One of the most significant financial threats to enterprises is ransomware attacks that encrypt data and disrupt operations — experts estimate the total average cost of a ransomware incident at $5.08 million. However, that’s not the only danger enterprises face: phishing campaigns employ social engineering tactics to steal user credentials. Supply chain attacks compromise trusted vendors to breach multiple organizations simultaneously. And insider threats from malicious or careless employees create risks that perimeter defenses can’t stop.
What tools are essential for enterprise cybersecurity?
Smart enterprises use various tools to keep data, systems, and networks safe.
- Endpoint protection to secure devices
- Firewalls and intrusion prevention systems to guard networks
- Identity and access management to limit access
- SIEM platforms to aggregate security data for analysis
- Cloud security tools to protect workloads in public cloud environments
How is enterprise cybersecurity different from SMB security?
Enterprises face a level of complexity that small businesses rarely encounter: thousands of employees across multiple locations, diverse technology stacks that span legacy systems and cloud platforms, stringent regulatory requirements, and sophisticated threat actors who target valuable data with sustained campaigns. That’s why enterprises need a cybersecurity approach with dedicated security teams, formal governance structures, and specialized tools.
What’s the difference between proactive and reactive enterprise security?
Proactive security aims to anticipate threats and prevent attacks, enabling you to identify and address weaknesses before they can be exploited. Conversely, reactive security responds to incidents after they happen through containment and recovery.
How should enterprises approach third-party/vendor risk management?
Classify vendors based on data access and business criticality. For example, high-risk vendors require detailed security assessments, while low-risk relationships need basic due diligence. Additionally, incorporate security requirements into procurement processes and contracts and conduct initial assessments before onboarding, as well as periodic reviews throughout the relationship.
What does a strong enterprise incident response plan look like?
An effective enterprise incident response plan defines roles and responsibilities for security teams, IT operations, legal, communications, and executives. It establishes clear procedures to detect, contain, eradicate, recover, and perform post-incident analysis.
Conclusion: Building a Strong Enterprise Cybersecurity Posture
Key Takeaways for Business Leaders and CISOs
No single tool can provide complete protection —enterprise cybersecurity requires a sustained investment in people, processes, and technology. To create resilience against evolving threats, use layered defenses that combine prevention, detection, and response. And use risk management frameworks to help prioritize cybersecurity investments based on their potential business impact.
Remember, security works best when integrated into business processes from the start. Executive sponsorship ensures adequate funding and helps resolve conflicts. And culture matters as much as technology. Employees who understand security responsibilities become your first line of defense.
Next Steps: Building a Proactive Security Posture
Ready to build a proactive security posture?
- Conduct a gap analysis, identifying your organization’s critical assets
- Evaluate your current controls against a recognized framework like NIST CSF or CIS Controls
- Engage a managed partner like Xantrion
Additionally, invest in employee training programs that engage staff beyond merely checking compliance boxes. Test incident response procedures through tabletop exercises before real crises demand flawless execution. And develop relationships with potential partners before emergencies require rushed decisions.
Exploring Enterprise Cybersecurity Services with Xantrion
Your security posture is only as strong as your ability to detect and respond to threats around the clock. And finding the right cybersecurity vendor can make or break your security efforts. Xantrion’s enterprise cybersecurity services provide 24/7 managed detection and response, vulnerability management, and compliance support that scale with your organization’s growth.
Whether you’re supplementing your existing security team or building capabilities from scratch, partnering with Xantrion brings immediate expert support. Get in touch today to learn more about how our managed security services can help keep threats at bay.

