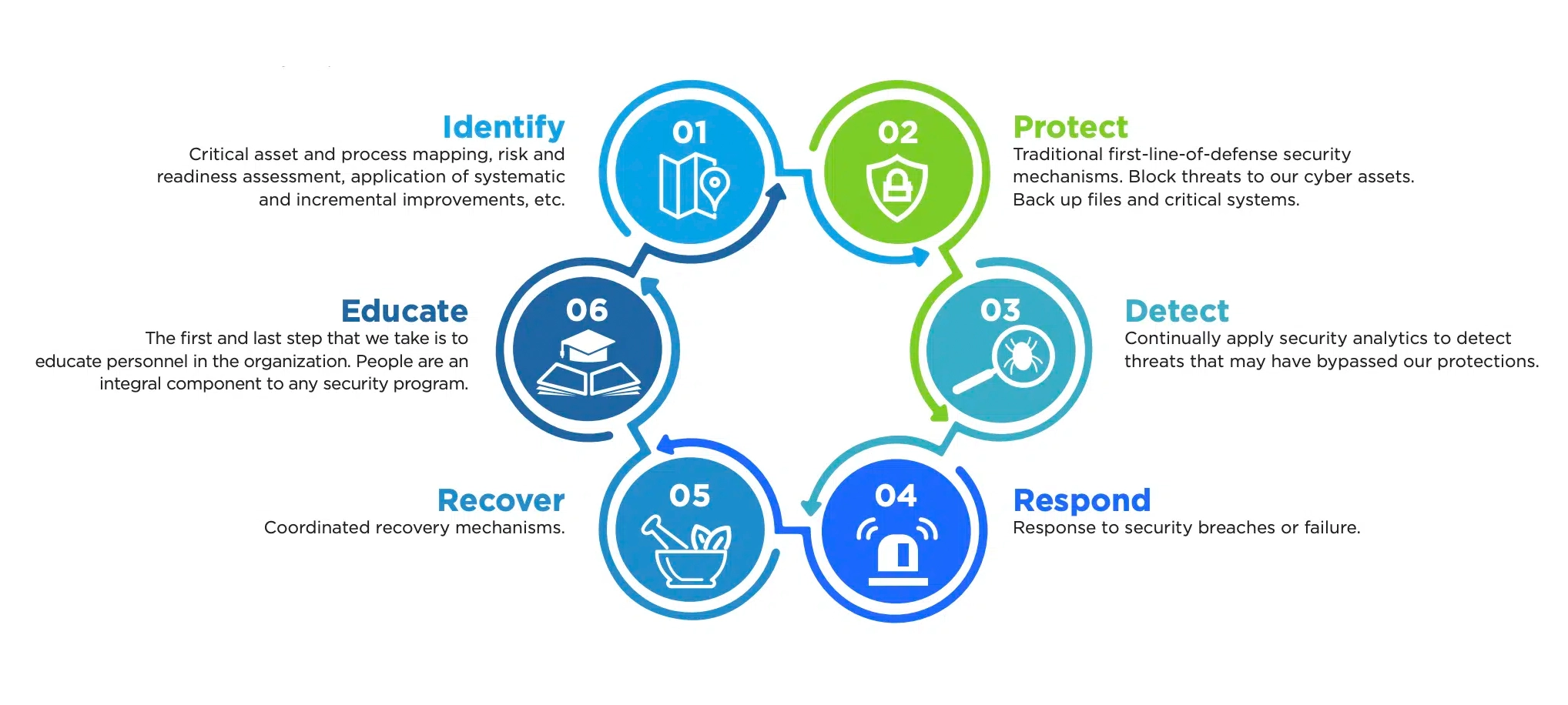
The business impact of cyber incidents like ransomware attacks make it critical for companies to take action to lower their cyber risks and to avoid becoming the next victim. Companies must also be pragmatic and develop a strategy for dealing with the ramifications of a cyber incident should one occur. Reducing cyber risk, while imperative, does not guarantee that persistent threat actors will always be blocked. The potential of a cyber incident still exists. Therefore, companies should adopt a cyber resilience framework that includes multiple elements of prevention and the ability to recover.
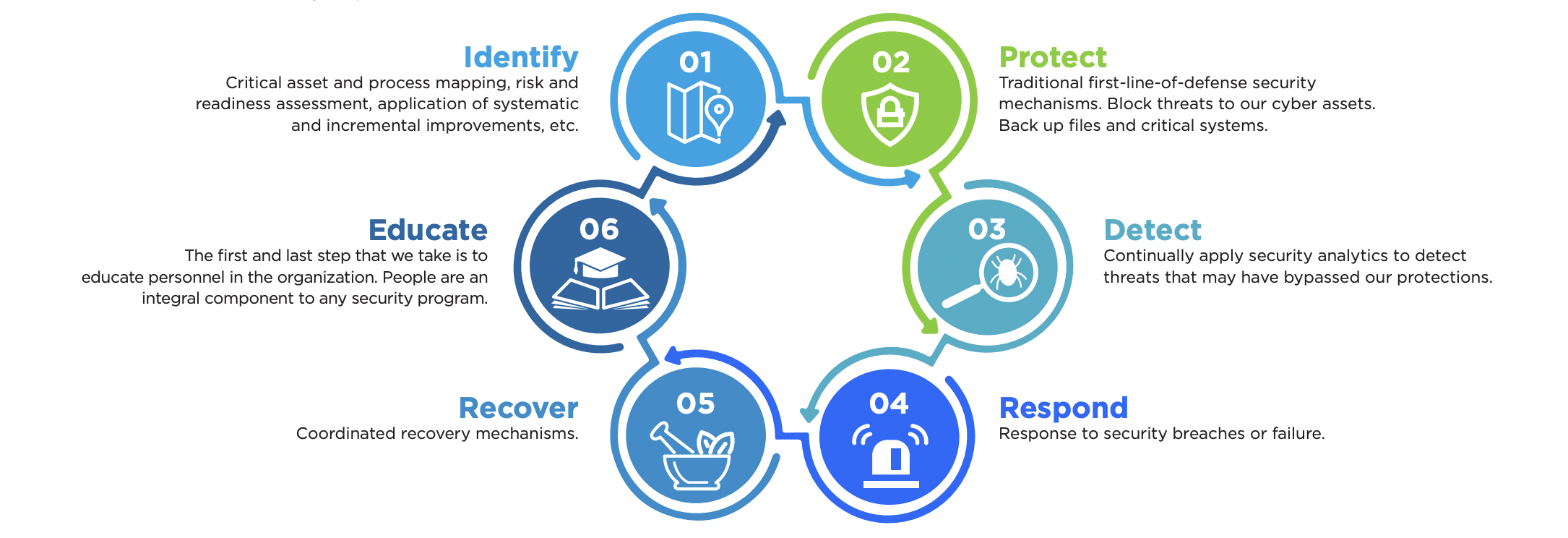


From Framework to Action
Unless implemented, a framework is just a blueprint. Companies must convert this blueprint into structure. But not all companies have the time or internal talent to effectively accomplish this conversion. Moreover, it’s important that businesses don’t underestimate the value of cyber criminal experience. Often, criminals use tactics that have worked many times over. This is how threat actors make their nefarious businesses profitable.
From Framework to Action Option 1: Do-It-Yourself
Business leaders and employees assigned cybersecurity oversight should leverage this cyber resilience framework as a confidence assessment guide. Answering the questions below will provide clarity about what your organization can accomplish on its own versus what should be accomplished with the assistance of a managed service provider.
Does my company have the technologies and internal processes in place to complete each of these steps? It’s critical for companies to understand where they stand in terms of executing on each step. Companies should address the steps where they fall short with internal task forces. For example, if a company has not formalized cybersecurity employee training, it should establish an education curriculum and ensure employees complete it.
When was the last time these technologies and processes were evaluated for effectiveness? Companies should regularly assess each step in the framework to ensure it is suitable with changing conditions. For example, for the Detect step, companies should take note of new forms of attacks and update their systems and processes so that they are prepped to respond if attacked.
If a cybersecurity incident or incidents have occurred, what was learned about our company’s state of cyber resilience, and were there any deficiencies? If an incident occurs, companies should have a debriefing process to uncover how the adversary succeeded and the systems and processes the company needs to put in place to strengthen cyber resilience.
If cyber resilience deficiencies were identified, what has been our company’s track record in closing these deficiencies in a timely manner? Once a company has identified deficiencies and the steps to erase them, follow-up should occur to confirm the steps produced the intended outcome. As an example, systematic backup is crucial but the process is incomplete unless restoration is also tested.
What is our level of confidence in critically evaluating our current set of cyber reliance technologies and alternatives? Internal confidence can sometimes be excessive. With the considerable knowledge, processes, and technologies required for effective cyber resilience, bringing in a third party to assess your state of cyber resilience can assist in identifying deficiencies and provide a point of view that might otherwise be missed by internal staff.
If new or replacement technologies are needed, can our company manage the end-to-end process of evaluating and implementing change in a reasonable period of time and minimize impact on employees? The more transformative new or replacement technology is, the greater the likelihood that bumps will be encountered on the road to deployment. Conduct a technology gap analysis on your company’s cyber resilience and keep in mind that the larger the gap, the more your internal project management capabilities will be tested. Remember, threat actors are not waiting for you to deploy new and better technology to strengthen your cyber resilience before they pounce.
From Framework to Action Option 2: Managed Services Providers
Hire a managed services provider (MSP) to conduct the assessment above in collaboration with their customers and prospects. But before you can get to an actual assessment, education on cyber resilience is critical and should cover the following:
- What cyber resilience entails.
- How your customers and prospects can use your talent, services, and technology to achieve it.
- The potential ramifications if customers do not follow a cyber resilience framework.
Cyber resiliency should be seen as part of an organization’s wider risk management and business resilience strategy. It is a worthwhile but often confusing endeavor for companies. Fortunately, cyber resilience frameworks are available to guide you. Contact Xantrion, we can help your business implement the six stages of cyber resiliency so you can be prepared when and if a cyber attack occurs.