Imagine this: It’s a typical Wednesday morning when your systems suddenly go dark. Hackers have stolen your customer database, phones are ringing nonstop with panicked clients, and regulators are raising eyebrows.
For many businesses, this nightmare is a reality. However, the good news is that most of these disasters are preventable through regular cybersecurity audits and regular checkups that identify problems before they escalate into catastrophes. A cybersecurity audit examines your organization’s digital defenses, policies, and procedures to identify vulnerabilities before malicious actors do.
Here’s everything you need to know about cybersecurity audits: what they are, why they’re important, and what to expect during the audit process.
What Is a Cybersecurity Audit?
Is a cybersecurity audit the same as a regular IT audit? Not quite. Here’s how they’re different.
- General IT audits review everything technology-related, including servers, network performance, software licenses, hardware inventory, and whether someone has remembered to update the office printer drivers.
- Cybersecurity audits narrow the scope dramatically, focusing exclusively on security-specific elements: who can access what data, how well your information is encrypted, whether your incident response plan would actually work during a crisis, and how quickly you can detect threats.
- Penetration tests are a valuable complement that tests whether your security controls actually work under attack conditions. They simulate real attacks so you can identify (and proactively address) technical vulnerabilities.
A cybersecurity audit evaluates your organization’s information security policies, procedures, and technical controls. During a cybersecurity audit, an auditor examines how well your current security measures protect against cyber threats, data breaches, and unauthorized access.
Why Cybersecurity Audits Are Important
Cyberattacks now cost companies an average of $4.4 million per breach, according to IBM’s latest “Cost of a Data Breach” Report. While smaller businesses may not face losses quite that steep, they often suffer disproportionately because they have fewer resources to recover from a breach of any size. Regulatory fines can add hundreds of thousands or millions more to the bill. And customer trust? Once it’s gone, it can take years to rebuild, if ever.
The benefits of cybersecurity audits are numerous.
- Regular audits can help teams stay ahead of risks, allowing you to identify weak spots before attackers exploit them. It’s like finding out your roof has loose shingles before the next storm, not after water damages your whole office.
- Compliance audits serve as proof to regulators that you’re taking security seriously. When investigators start asking hard questions about your data protection practices, you’ll have documentation showing due diligence rather than scrambling to explain why you didn’t know about obvious vulnerabilities.
- Audits also help customers feel more confident. Major clients are increasingly requiring security assessments before signing contracts, seeking confidence that partnering with you won’t expose their data to unnecessary risks. Having recent audit results can fast-track these conversations and help close deals quickly.
Business continuity depends on having security measures that work under pressure. When audits reveal gaps in backup systems or incident response plans, you can fix them during calm periods rather than in a crisis. Insurance companies have caught on, requiring security audits to maintain coverage or receive favorable premium rates. In fact, some insurers now mandate specific security controls based on audit findings.
Don’t underestimate reputation protection either. Public data breaches generate headlines that damage brand trust and customer relationships for years. Proactive auditing demonstrates to stakeholders that you invest in prevention, not just damage control.
Types of Cybersecurity Audits
All audits are not created equally. Understanding the differences can help you select the most suitable approach for your specific situation and budget.
Internal vs. external audits:
- Internal audits use your own staff or trusted consultants to review security controls, and your organization maintains complete control over timing, scope, and confidentiality.
- External audits bring in independent third parties who provide objective assessments and industry benchmarking. They often spot issues that internal teams miss due to familiarity bias.
Regulatory-driven requirements:
- Healthcare organizations must comply with HIPAA security rules.
- Financial services firms face SOX requirements that can shut down operations if ignored.
- Retailers that handle credit cards must comply with PCI DSS or risk losing their payment processing abilities.
- Government contractors must meet specific federal security standards or risk losing their contracts.
Technical vs. administrative scope:
- Technical audits dive deep into firewalls, encryption protocols, network configurations, and system hardening.
- Administrative audits review policies, procedures, employee training programs, and governance structures to ensure compliance.
- Risk-focused audits prioritize your most critical assets and realistic threat scenarios.
- Compliance-focused audits verify that you meet specific regulatory requirements.
The Cybersecurity Audit Process
Effective audits minimize business disruptions while maximizing security insights. The process typically spans four to twelve weeks, depending on your organization’s size and complexity.
- Planning: During the planning stages, auditors will collaborate with your team to define the scope, identify critical systems, and schedule activities that align with your business operations. You’ll need to provide network diagrams, policy documents, system inventories, and organizational charts.
- Evidence collection: After planning, auditors interview key personnel, review documentation, examine system configurations, and observe daily operations. They should minimize operational impact during this phase, working around maintenance windows and busy periods.
- Testing: During testing, auditors verify that your documented policies are effective in practice. Auditors may attempt to access restricted systems, review user permissions, test backup procedures, or simulate security incidents.
- Reporting: At the conclusion of the formal audit process, you’ll receive a detailed findings report that explains discovered vulnerabilities, assesses their risk levels, and provides specific remediation recommendations.
At Xantrion, we’ve found that small businesses with straightforward technology typically complete audits in four to six weeks. Mid-sized organizations need six to ten weeks for thorough assessments. Large enterprises might require three months or more for comprehensive evaluations that cover multiple locations and complex systems.
Additionally, Xantrion provides numerous deliverables, including:
- Comprehensive findings report with an executive summary
- Detailed technical findings
- Issue-based risk assessments
- Prioritized remediation plan
- Leadership team presentation
- Follow-up consultations to clarify recommendations
Thinking about outsourcing cybersecurity? Xantrion can help. Our security experts give your small or medium business access to enterprise-grade resources at budget-friendly prices. Learn more.
Cybersecurity Audit Scope & Frameworks
Defining your audit scope helps you avoid wasting effort and ensures you comprehensively cover your actual risks. Your scope should encompass:
- Technical infrastructure
- Personnel policies
- Operational procedures
- Governance frameworks
Most audits follow established frameworks that provide structured approaches to security evaluation. Common frameworks include:
- The NIST Cybersecurity Framework offers six core functions: Govern, Identify, Protect, Detect, Respond, and Recover.
- ISO 27001 provides comprehensive information security management standards that are internationally recognized.
- The Government Accountability Office (GAO) framework focuses on federal requirements but offers valuable guidance for any organization.
- COBIT addresses governance and risk management from a business perspective rather than a purely technical viewpoint.
Additionally, industry-specific requirements often determine which frameworks make most sense for your situation. For example:
- Healthcare organizations typically align with NIST guidelines while ensuring HIPAA compliance.
- Financial services firms may use FFIEC guidelines that address banking-specific risks.
- Government contractors follow NIST 800-53 controls that can seem overwhelming but provide thorough security coverage.
Cybersecurity Audit and Compliance
Regulatory compliance drives many audit requirements, and understanding the relationship between audits and various regulations helps you plan more effectively and avoid costly surprises.
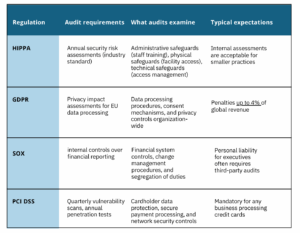
The key difference between regulatory requirements and voluntary frameworks lies in flexibility and enforcement. Voluntary frameworks, such as NIST, offer implementation flexibility, enabling you to tailor controls to your specific environment and risk tolerance. You can then select the recommendations that are most suitable for your business.
Regulatory frameworks mandate specific controls with less room for interpretation. You must implement the required safeguards, regardless of whether you believe they apply to your situation.
Cybersecurity Audit Checklists & Best Practices
Effective audits systematically address core security areas. While each organization faces unique risks, certain security fundamentals apply universally and need regular attention.
Core security areas auditors examine
Use this checklist to prepare for audits and identify potential gaps before auditors arrive.
Access controls
- User account management and regular access reviews
- Password policies and multi-factor authentication requirements
- Privileged access procedures for administrators
- Role-based permissions aligned with job functions
System patching and vulnerability management
- Documented vulnerability scanning and assessment processes
- Patch testing procedures before production deployment
- Update deployment timelines with priority classifications
- Emergency patching procedures for critical vulnerabilities
Data encryption and protection
- Encryption for data in transit (network communications)
- Encryption for data at rest (stored files and databases)
- Key management procedures and secure storage
- Verification of encryption strength and implementation
Vendor risk management
- Security assessments of third-party providers
- Contract security terms and liability clauses
- Ongoing vendor monitoring and performance reviews
- Supply chain security requirements and verification
Network segmentation and security
- Traffic control policies between network segments
- Firewall rule effectiveness and regular reviews
- Breach containment capabilities and network isolation
- Monitoring of network communications and anomalies
Incident response planning
- Documented incident response procedures and playbooks
- Staff training on security roles and responsibilities
- Communication protocols for internal and external stakeholders
- Regular testing and recovery drills
Best practices for audit success
Following these practices year-round makes audits smoother and demonstrates an ongoing commitment to security rather than last-minute compliance efforts.
Preparation throughout the year
- Schedule quarterly internal security reviews to catch issues early
- Maintain current documentation for all policies and procedures
- Keep system configuration records updated in real-time, not just before audits. Hint: A managed cybersecurity service provider like Xantrion can help you streamline and automate this process
Staff readiness
- Train employees on their specific security responsibilities and how they relate to audit requirements
- Conduct mock audit sessions to prepare teams for questions and processes
- Designate clear points of contact for auditors to streamline communication
Operational continuity
- Establish dedicated communication channels with audit teams, separate from daily operations
- Plan audit activities around critical business operations and maintenance windows
- Prepare secure workspace access for external auditors without compromising security
Responding to a Cybersecurity Audit
Receiving your audit results can feel overwhelming, especially if the report contains dozens of findings with technical jargon and unfamiliar risk ratings. Audit findings typically classify issues by risk level using standard categories: critical, high, medium, and low.
- Critical findings represent significant security gaps that could lead to immediate data breaches or system compromises. These require immediate attention and emergency budget allocation.
- High-risk issues need remediation within 30-60 days to prevent serious security incidents.
- Medium- and low-risk findings can often be addressed during scheduled maintenance windows or regular budget cycles, but shouldn’t be ignored indefinitely.
Good auditors will explain what needs fixing and why it matters for your business, and they’ll also pinpoint how to implement solutions within your constraints. Don’t hesitate to challenge any findings that seem irrelevant to your risk environment or budget realities.
To get the most out of your audit, approach it not as tedious compliance overhead, but as an opportunity to enhance business value. For example, audit findings may help you justify security investments to leadership teams, boost operational efficiency by addressing process gaps, or demonstrate your security commitment to customers and partners. Also, be sure to include board members and executive leadership in audit discussions.
Future of Cybersecurity Audits
Like everything else in technology, audit requirements keep shifting. Their regulations and expectations adapt as new tools appear and different risks emerge. Automation is fundamentally reshaping how audits are conducted and what they can accomplish. For example:
- Continuous monitoring tools can check security configurations constantly rather than annually, identifying drift from approved settings in real-time.
- Artificial intelligence enables auditors to analyze larger datasets and identify subtle patterns that manual reviews might overlook.
- Automated evidence collection reduces audit duration and human error while improving consistency across different auditors and time periods.
Additionally, as organizations distribute systems across multiple providers and hybrid environments, cloud security audits are becoming more complex. Audit approaches must focus on identity management, data governance, and cloud-specific security controls, rather than relying on traditional network boundaries.
Choosing an External Cybersecurity Audit Provider
External auditors provide independence and specialized expertise that internal teams often lack, but require significant coordination and budget allocation. Consider engaging an external auditor when:
- Regulations require third-party assessments
- You need objective perspectives on security programs that internal teams can’t provide
- Internal resources lack specific audit skills for your industry or technology environment
- Major clients demand it; some organizations request independent audit results before signing contracts or renewing partnerships
As with most other services, you get what you pay for. Select your auditors based on their relevant qualifications and industry experience, rather than choosing the one with the lowest cost proposal.
Look for certifications like Certified Information Systems Auditor (CISA), Certified Information Security Manager (CISM), or Certified Public Accountant (CPA) with an IT audit specialization. And don’t underestimate the power of industry experience. Healthcare auditors understand HIPAA requirements, while financial services auditors are familiar with banking regulations and the expectations of examiners.
For credible audit results that stakeholders will trust, auditor independence is crucial. Avoid auditors who sell security products or services that they might recommend during audits, as this creates obvious conflicts of interest. Be wary of firms that promise specific outcomes before starting work or seem more interested in finding problems to fix than in providing objective assessments of your current security posture.
FAQs on Cybersecurity Audits
How long does a cybersecurity audit take?
Audit duration depends primarily on your organization’s size, the complexity of your systems, and the scope of the audit requirements. Small businesses with straightforward technology and limited regulatory requirements typically complete audits in four to six weeks.
Mid-sized companies with multiple locations or complex systems may need six to ten weeks for thorough assessments. Large enterprises may take 12 weeks or more to evaluate multiple business units and geographic locations.
Additionally, it’s worth noting that initial audits always take longer than follow-up assessments since auditors must learn your systems, processes, and organizational culture from scratch. Thankfully, subsequent audits can move more quickly, focusing on changes since the last assessment and previously identified remediation efforts.
What happens during a cybersecurity audit?
Auditors review your security policies and procedures, interview key personnel across different departments, examine system configurations and network architecture, and test security controls to verify they work as documented. You’ll need to provide extensive documentation, including network diagrams, policy manuals, incident reports, and system inventories.
Expect auditors to request access to critical systems for configuration review, though they shouldn’t disrupt normal operations. They typically work on-site for portions of the assessment but can complete much of their analysis and documentation remotely.
What is the difference between an IT audit and a cybersecurity audit?
IT audits examine all technology systems, including hardware inventory, software licensing, network performance, system availability, and general technology governance. They focus on operational efficiency, cost management, and technology alignment with business objectives.
Cybersecurity audits focus specifically on security controls, threat management, and risk reduction activities. They examine access controls, threat detection capabilities, incident response procedures, and data protection measures. In other words, cybersecurity audits are specialized IT audits that concentrate exclusively on protecting information and systems from unauthorized access, modification, or destruction.
Do small businesses need cybersecurity audits?
Small businesses face the same cyber threats as large organizations, but often have fewer resources for security. Regular audits can help your small business identify affordable security improvements that provide maximum risk reduction within budget constraints.
Many cyber insurance policies now require annual security assessments regardless of company size, making audits a business necessity rather than an option. Customers increasingly expect security due diligence from all vendors, not just large corporations. Regulatory requirements and state privacy laws apply to small businesses that handle sensitive data.
Does a small accounting firm need the same comprehensive audit as a major hospital system? No, but they both need some level of security assessment. Rather than skipping audits entirely due to cost concerns, scale your audit investment to match your risk exposure and budget constraints.
Xantrion helps businesses prepare for and navigate cybersecurity audits with confidence. Contact us to discuss how our audit prep services can help you protect your organization.

