Choosing the right cybersecurity framework can feel overwhelming. You’re juggling customer demands, regulatory requirements, and budget constraints while trying to build a security program that works. Three frameworks consistently rise to the top of most organizations’ consideration lists: ISO 27001, SOC 2, and NIST Cybersecurity Framework.
Each framework serves different purposes and audiences. Pick the wrong one, and you may end up wasting months of effort and thousands of dollars on something that doesn’t meet your business needs. But if you get it right, you’ll have a foundation that opens doors to new customers while improving your security posture.
Let’s take a closer look at these frameworks, exploring what each offers, who uses them, and how to choose the right path for your organization.
Quick Definitions (What Each One Is & Who Uses It)
Before diving into comparisons, it’s important to understand what each framework does and who typically uses it.
- ISO 27001 is an international Information Security Management Systems (ISMS) standard. When you get ISO 27001 certified, you’re proving to the world that you have a disciplined approach to managing security risks across your entire organization. Think of it as demonstrating that security isn’t just something your IT team handles; it’s woven into how your business operates.
- SOC 2 provides attestation (but not certification) for service organizations that handle customer data. Unlike ISO 27001, you won’t receive an SOC 2 certificate; instead, you will get a report showing how well you protect customer data. These confidential reports require non-disclosure agreements when you share them with prospects or customers.
- The National Institute of Standards and Technology has two offerings: the NIST Cybersecurity Framework (CSF), which offers voluntary guidance for managing cybersecurity risks, and NIST SP 800-53, which provides a detailed catalog of security controls. While NIST started in government circles, plenty of private companies now use these frameworks too.
Geography also has an impact on which framework may be your best choice.
- ISO 27001 works everywhere; it’s a truly global framework. If you’re doing business internationally, especially in Europe, ISO 27001 carries serious weight.
- SOC 2 dominates in the United States, particularly among SaaS companies and cloud service providers.
- NIST frameworks traditionally serve government agencies and contractors, though private sector adoption continues to grow.
ISO 27001 vs SOC 2: Scope, Output, Cost & Timelines
If you’re comparing ISO 27001 vs SOC 2, some basic differences can help make your choice clearer.
- Scope differences: ISO 27001 looks at your entire organization. It wants to understand how security integrates into every aspect of your business, from HR processes to vendor management, and how your executives make decisions. In contrast, SOC 2 zeros in on specific systems and processes that handle customer data. It’s more focused, but also narrower in scope.
- Output variations: With ISO 27001, you get a certificate valid for three years. You can use that certificate in your marketing, promote it on your website, and include it in your proposals. SOC 2 gives you a report, either Type I (a snapshot in time) or Type II (which covers a period, usually six to 12 months). One common question we hear is, “Is SOC 2 a certification?” No, it isn’t. SOC 2 produces attestation reports from CPAs, not certificates from certification bodies. And unlike ISO 27001 certification, these reports must remain confidential unless you choose to share them under an NDA.
- Timeline considerations: Implementing ISO 27001 typically takes 12 to 18 months from start to finish. You must build your management system, implement controls, document everything, and pass two audit stages. SOC 2 readiness typically takes six to 12 months to implement, during which time your controls are designed and operationalized. For Type II reports, you then need to demonstrate that those controls operated effectively for an additional six to 12-month audit period.
- Cost analysis: ISO 27001 costs vary wildly based on your size and complexity. According to Secureframe, preparation, implementation, and audit costs can range between $15,000 and $90,000. Preparing for and completing an SOC 2 examination typically runs $10,000-$150,000.
Still uncertain as to which framework is the best fit? If you need global credibility, have international customers, or want comprehensive security management, choose ISO 27001. Opt for SOC 2 when your customers (especially in the U.S.) specifically ask for it, or when you’re in SaaS, cloud services, or other service provider industries. It’s worth pointing out that many organizations eventually do both. For example, you may start with SOC 2 to meet immediate customer demands, then add ISO 27001 when you expand globally.
ISO 27001 vs NIST (CSF & 800-53): Risk vs Technical Depth
NIST’s Cybersecurity Framework comprises six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. Each function breaks down into categories and subcategories that you can customize based on your specific risks and business needs. Meanwhile, Special Publication 800-53 takes an entirely different approach; it’s a massive catalog of security controls (1000+ across 20 different families). NIST’s Risk Management Framework (RMF) walks you through how to select, implement, and continuously monitor these controls.
NIST shines when it comes to technical depth. While ISO 27001 offers numerous general, high-level controls, NIST 800-53 provides incredibly detailed guidance on how to implement specific technical safeguards.
Is there a significant overlap between the frameworks? Yes. Various studies show 80 to 96% overlap, but the wide range depends on what you’re measuring. For example, when researchers look at broad concepts like whether both frameworks address access control or incident response, they find high overlap (closer to 96%). But when they try to map specific controls one-to-one, the overlap drops significantly (closer to 80%)
Many security professionals combine these approaches rather than choosing one or the other. The reality is that ISO controls are often too general for organizations that need NIST’s level of technical specificity, but the frameworks work well together as complementary tools. Use ISO 27001 for the management system structure and risk-based thinking, then implement NIST 800-53 controls for the technical details. Your Statement of Applicability in ISO 27001 can reference detailed NIST control implementations.
ISO 27001 vs ISO 27002 (and 2013 vs 2022 Update)
The relationship between ISO 27001 vs 27002 may initially seem confusing, but it’s actually straightforward once you understand the role that each plays.
- ISO 27001 is the requirements standard: It’s the one you get certified against. It tells you what you must have in your management system.
- ISO 27002 is the implementation guide: It provides ideas and best practices for implementing security controls, but it does not certify to ISO 27002.
The 2022 updates, which became mandatory for certified organizations in October 2025, changed the control structure. The old version had 114 controls in 14 categories. The new version has 93 controls organized into four themes: organizational, people, physical, and technological. There are also controls in new areas, such as threat intelligence and cloud services security.
Do you have existing documentation based on the 2013 structure? If so, you’ll need to map it to the new 2022 framework. ISO provides mapping documents, but you’ll still need to review everything to ensure you cover the updated requirements.
ISO 9001 vs 27001: Do You Need Both?
The ISO 9001 vs 27001 comparison boils down to Quality Management Systems versus Information Security Management Systems. Both use similar management system structures, which creates opportunities for efficiency.
ISO 9001 addresses quality management across your organization, focusing on customer satisfaction and continuous improvement. ISO 27001 specifically targets information security risks but applies those same management principles to security processes. Think of it as taking the methodical approach you use for quality and applying it to cybersecurity.
If you already have ISO 9001, you can leverage a lot of that foundation. Processes like policy management, internal audits, corrective actions, and management reviews can serve both standards. And you can often expand the document control systems, training programs, and governance structures you’ve built for quality to cover security requirements, too.
Companies with existing ISO 9001 certifications often find that ISO 27001 implementation goes faster because they already understand how management systems work. However, security comes with its own unique requirements that cannot be simply added to existing quality processes. You’ll still need security-specific policies, risk assessments, and technical controls that exceed what ISO 9001 covers.
Choosing the Right Path (Decision Matrix & Scenarios)
Picking the right framework is about more than determining which framework has the most features; it’s finding the framework that best fits your business needs. Use this decision matrix to help evaluate your options:
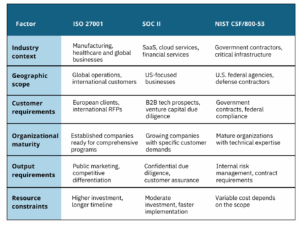
Still not sure which framework to choose first? Here are three typical paths organizations take, showing how business context drives framework priorities:
- U.S. SaaS company: Start with SOC 2 Type II to meet immediate customer demands, then add ISO 27001 when you expand internationally.
- European B2B technology company: Begin with ISO 27001 for credibility in EU markets, then consider SOC 2 later for U.S. expansion.
- Government contractor: Implement NIST CSF and 800-53 controls first, then potentially add ISO 27001 to take advantage of commercial opportunities.
Certification & Compliance Processes Compared (Step-by-Step)
Understanding how each framework’s process works helps you plan your timeline and resources more effectively.
ISO 27001 Certification & Compliance Process at a Glance
Stage 1 → remediation → Stage 2 → surveillance (yrs 1–2) → re-certification (yr 3)
The ISO 27001 process follows a two-stage audit conducted by accredited certification bodies. Stage 1 reviews your documentation policies, procedures, and risk assessments to ensure you’re ready for the operational audit. You’ll get a list of findings to address before moving forward.
After fixing any issues, Stage 2 evaluates whether your management system works in practice. Auditors interview staff, observe processes, and review evidence of how you handle security day-to-day. Pass this stage, and you’ll get your certificate, which is valid for three years.
To ensure you maintain and improve your system, your certification body conducts surveillance audits in years one and two. Re-certification audits in year three are comprehensive reviews similar to the initial Stage 2 audit.
SOC 2 Certification & Compliance Process at a Glance
Readiness → Type I/II planning → audit window → renew annually
SOC 2 starts with readiness assessments to identify gaps in your control design and implementation. You need to have effective controls in place before the formal examination begins.
Type I/II planning involves selecting which Trust Services Criteria apply to your services, defining what systems are in scope, and establishing your audit period. Type I focuses on control design at a specific point in time, whereas Type II evaluates your operating effectiveness over a period of six to 12 months.
During the audit window, auditors collect evidence that shows your controls operated effectively throughout the period. You’ll need annual renewals to keep your reports current and address any system or control changes.
NIST Certification & Compliance Process at a Glance
NIST Cybersecurity Framework adoption remains voluntary for most organizations. You can implement whichever parts make sense for your risk profile and business objectives. There’s no certification process; you’re essentially self-declaring your framework alignment.
But for many federal agencies and contractors, compliance with NIST 800-53 and RMF processes is mandatory, not voluntary. The Risk Management Framework guides your organization through control selection, implementation, assessment, authorization, and continuous monitoring. It’s a comprehensive lifecycle approach from system design through retirement.
Where They Overlap (and Where They Don’t)
Certainly, there’s a good amount of overlap between the frameworks: All three emphasize confidentiality, integrity, and availability (CIA) as core security principles. And they all require risk-based management approaches where you identify, assess, and treat security risks according to your organization’s risk tolerance. Additionally, leadership commitment and continual improvement feature prominently across all frameworks.
But as previously mentioned, those overlap statistics you see depend entirely on how the frameworks are measured. Conceptual alignment scores higher than specific control mappings. In practical terms, overlap depends on how deeply you implement each framework and how you interpret the requirements.
To maximize efficiency, use a shared approach. Policy libraries, centralized logging, coordinated access reviews, security training programs, incident response procedures, and vendor risk assessments can often satisfy multiple framework requirements simultaneously.
Are there areas where the frameworks diverge? For instance, ISO 27001’s management system requirements definitely exceed what SOC 2 and NIST cover. SOC 2’s Trust Services Criteria address specific service organization concerns that other frameworks don’t touch. NIST 800-53’s technical control depth far exceeds that of ISO 27001 and SOC 2.
Community & Practitioner Perspectives (Reddit)
Security professionals love debating framework choices online, and their insights are often more practical than official guidance. For example, Dr. Ron Ross, the gentleman who architected the NIST Risk Management Framework, has explained why NIST didn’t simply adopt ISO 27001.
When NIST began developing SP 800-53 around 2004-2006, it conducted extensive research comparing global standards, including ISO 27001 and 27002. The decision came down to control specificity: NIST found that ISO 27001 operated at too high a level of generality for its needs. NIST required detailed controls capable of addressing specific technical areas like multi-factor authentication, encryption standards, and boundary protection areas, where ISO 27001 lacked sufficient granular guidance. Rather than compromise on the technical depth their users needed, NIST developed its own comprehensive control catalog.
Many practitioners now advocate for blended approaches that combine both frameworks’ strengths. They’ll use ISO 27001’s management system structure as the foundation, then implement NIST 800-53 controls for technical depth. It’s like having the best of both worlds: organized risk management plus detailed implementation guidance.
Community discussions frequently warn against relying too heavily on AI-generated framework summaries and mappings. Always verify against official documentation. The Secure Controls Framework (SCF) provides useful crosswalks between multiple frameworks, but you should still validate mappings against your specific implementation.
Official & Authoritative Resources
When implementing frameworks or preparing for assessments, it’s best to stick to official sources for information and guidance:
ISO resources:
- ISO 27001:2022 Information Security Management Systems – Requirements
- ISO 27002:2022 Information Security Controls
- National accreditation bodies like ANAB or DAkkS provide certified auditor directories
NIST publications:
- NIST Cybersecurity Framework 2.0
- NIST SP 800-53 Security and Privacy Controls for Federal Information Systems
- NIST SP 800-171 Protecting Controlled Unclassified Information
AICPA resources:
- Trust Services Criteria for SOC 2 examinations
- AICPA audit and attestation guidance
- Licensed CPA directories for SOC examinations
Role in Due Diligence & Security Strategy
Cybersecurity frameworks are an important part of your organization’s ability to win new business and complete deals. Vendor risk management has made security attestations a standard requirement. When you respond to RFPs, you’ll routinely see requests for specific certifications: SOC 2 Type II reports for cloud services, ISO 27001 certificates for international vendors, or NIST framework alignment for government work. Procurement teams use these as a quick way to evaluate whether you meet their security standards.
Merger and acquisition processes also rely heavily on established cybersecurity frameworks during due diligence. Acquirers look at certifications as indicators of your security operations’ maturity and discipline. And companies with current certifications typically move through due diligence faster because they demonstrate organized risk management.
The key is staying prepared. Maintain current certifications, prepare comprehensive security documentation, and develop crosswalk mappings showing how your controls address multiple framework requirements. That way, if (and when) opportunity knocks, you can quickly and confidently respond.
Frequently Asked Questions
Do I need both SOC 2 and ISO 27001?
It depends. Many organizations eventually implement both frameworks, but you don’t need to start there. Focus on the framework that’s most critical to your immediate business needs. For example, if your U.S. customers constantly ask for SOC 2, start there. But if you’re planning to expand internationally? ISO 27001 may be your priority. Remember, you can add the second framework later as your business grows.
Which is harder to achieve — ISO 27001 certification or SOC 2 Type II attestation?
Good question. Because it’s a full management system, ISO 27001 typically requires more comprehensive organizational changes, while SOC 2 focuses more narrowly on specific controls. But the level of difficulty depends on your existing security maturity. If you already have good security practices, SOC 2 may feel more straightforward. If, however, you need to build systematic risk management, you may find ISO 27001’s structure more helpful.
How often do I need to renew each certification or assessment?
ISO 27001 certificates last three years with annual surveillance audits in between. SOC 2 reports should be renewed annually to stay current. Most customers will want to see reports that are less than a year old. NIST frameworks don’t have formal renewal requirements since they’re voluntary, but you should reassess and update your implementation regularly.
How much do ISO 27001, SOC 2, and NIST compliance cost?
Costs vary dramatically based on your organization’s size, complexity, and starting point. For example, ISO 27001 may cost anywhere from $10,000 for small companies to $500,000+ for large enterprises. SOC 2 typically runs $10,000 to $150,000 for initial Type II reports. NIST implementations depend entirely on scope; you may spend very little if you’re just aligning with the framework, or you can spend hundreds of thousands of dollars implementing comprehensive 800-53 controls. Your cybersecurity services company should be able to provide a general estimate.
How long does it take to prepare for each certification or framework?
Plan on 12 to 18 months for ISO 27001 from project start to certificate. SOC 2 readiness usually takes six to 12 months, plus your audit period. And as you’ve probably guessed, NIST framework implementation timelines vary widely based on what you’re trying to accomplish. Companies with existing security programs can move much faster than those starting from scratch.
Which framework should I start with if I have no certifications?
For help making an informed framework decision, look first at your customer base and industry. For example, U.S. technology companies often start with SOC 2 because that’s what their prospects ask for. International businesses frequently choose ISO 27001 for global credibility. And government contractors typically need NIST alignment. Don’t overthink it; pick the one that solves your organization’s most pressing problem.
Can these frameworks and standards be mapped to each other?
Absolutely. There’s significant overlap between different cybersecurity frameworks, so you can reuse policies, procedures, and evidence across multiple compliance programs. But remember, each framework has unique requirements that need specific attention. You can’t assume that checking one box automatically satisfies another framework’s requirements.
How does SOC 2 compare to ISO 27001 in terms of scope and recognition?
SOC 2 has a narrower scope but strong recognition in the U.S. market, especially for service providers. ISO 27001 covers your entire organization and carries global recognition. Ultimately, you should choose your starting framework based on where you do business and what your customers expect.
What is the NIST Cybersecurity Framework (CSF)?
The NIST CSF provides voluntary guidance for managing cybersecurity risks through six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. Unlike other frameworks, CSF provides flexible guidance that you can tailor to your specific situation, rather than a checklist of mandatory requirements.
How is NIST CSF different from ISO 27001?
NIST CSF offers flexible guidance for cybersecurity activities, while ISO 27001 provides specific requirements for a certifiable management system. NIST focuses on framework functions and what you should be doing. ISO 27001 emphasizes methodical management processes and how you should manage security across your organization.
The right security framework choice depends on understanding your business context rather than picking the “best” framework in abstract terms. Start with your immediate needs, but remember to consider where your business is heading. The framework that serves you well today should also support your growth tomorrow.

