Ransomware. Insider risks. System failures. Data breaches. Your organization faces no shortage of threats, but without a clear method to identify and evaluate those risks, you’re making security decisions in the dark. ISO 27001 risk assessment provides you with a structured process. It forms the backbone of any Information Security Management System (ISMS), providing a systematic approach to identifying, analyzing, and evaluating risks to your data’s confidentiality, integrity, and availability.
Risk assessment under ISO 27001 is a continuous process that aligns with certification requirements and drives ongoing ISMS improvement. Organizations use it to prioritize security investments, demonstrate compliance to stakeholders, and build resilience against evolving threats.
In this post, we’ll walk through the ISO 27001 risk assessment methodology, explore practical frameworks and templates, and provide examples that show how organizations might apply these principles. Whether you’re preparing for certification or strengthening your security posture, you’ll find actionable guidance for each phase of the risk assessment process.
What Is an ISO 27001 Risk Assessment?
An ISO 27001 risk assessment, defined in clause 6.1.2 of the standard, requires organizations to identify, analyze, and evaluate information security risks. You’re effectively answering three questions:
- What could go wrong?
- How likely is it to happen?
- What would the impact be?
The assessment serves as the foundation of your ISMS. Every control you implement, policy you write, and security decision you make should trace back to risks you’ve identified and evaluated. Without this foundation, you’re left to guess which security measures matter most to your organization.
ISO 27001 certification auditors will examine your risk assessment process. They want to see that you’ve established clear criteria for evaluating risks, that your methodology is consistent, and that you can demonstrate how your selected controls address identified risks. Related standards like ISO 27005 and ISO 31000 provide additional guidance on risk management methodology, though ISO 27001 remains the baseline for ISMS certification.
The benefits of an ISO 27001 risk assessment go beyond mere compliance, allowing your organization to:
- Prioritize limited security budgets by focusing resources on the threats that matter most
- Gain a common language for discussing security risks with leadership
- Establish a framework for continuous improvement, where each assessment cycle validates existing controls and reveals new risks
The ISO 27001 Risk Assessment Process
ISO 27001 risk assessment follows a structured five-step process:
- Establish your framework
- Identify risks and assets
- Analyze and evaluate risks
- Select treatment options
- Monitor for ongoing improvement
The ISO 27001:2022 standard requires specific elements in your risk assessment:
- Clear risk criteria that define how you’ll measure likelihood and impact
- A structured approach to risk identification, whether asset-based, scenario-based, or both
- Defined impact and likelihood scales that allow consistent scoring
- A methodology that produces comparable results over time
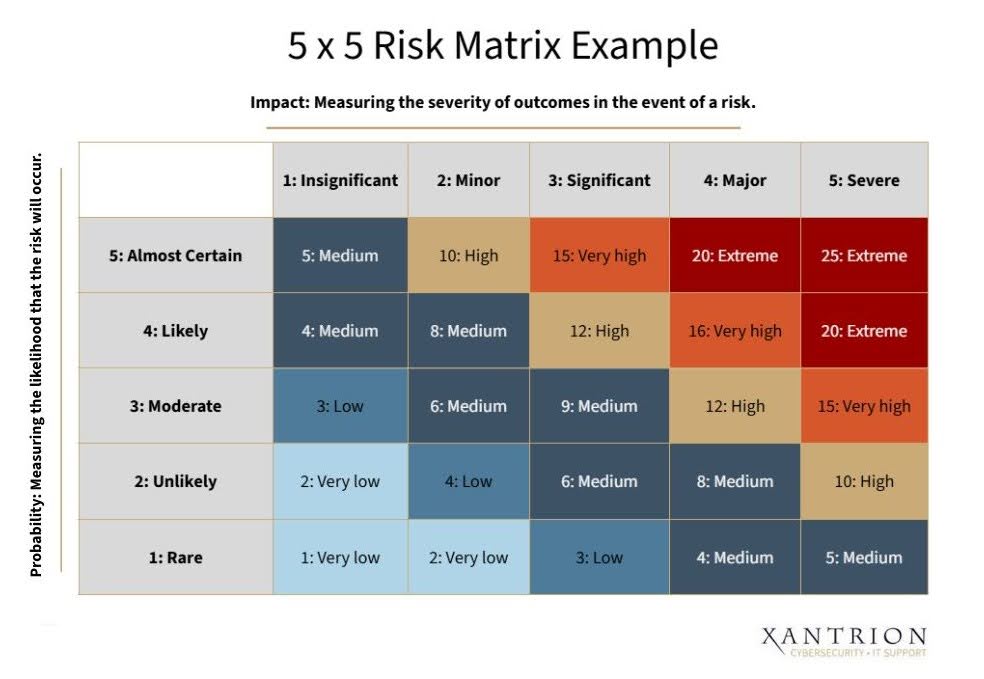
5×5 risk matrix example (1200 x 800 px) – 1
Many organizations use a qualitative approach with a 5×5 grid that scores likelihood and impact from very low to very high. The asset-threat-vulnerability model works well here: you identify an asset (like customer data), consider threats against it (like ransomware), and evaluate existing vulnerabilities (like unpatched systems). Multiply likelihood by impact, and you get a risk score that helps prioritize remediation efforts.
Let’s break down each step in detail.
Step 1 — Establish Your Risk Management Framework
Before identifying risks, define how you’ll measure and evaluate them. Your risk management framework spells out the baseline criteria, risk appetite, ownership structure, and scoring scales that will guide every subsequent decision.
Start with your risk appetite. How much risk is your organization willing to accept? For example, a healthcare provider handling patient records may have near-zero tolerance for confidentiality breaches, while a marketing firm may be willing to accept higher risks in some areas. Document these thresholds; you’ll use them to determine which risks require immediate treatment and which you can accept.
Define your likelihood and impact scales. A common approach uses five levels for each:
- Likelihood: Very low (rare), Low (unlikely), Medium (possible), High (likely), Very high (almost certain)
- Impact: Very low (minimal), Low (limited), Medium (moderate), High (significant), Very high (catastrophic)
You’ll also need to assign risk ownership. Every identified risk needs an owner — someone accountable for monitoring it and implementing treatment plans.
Remember, ISO 27001 requires that leadership is engaged, so top management must approve this framework. Once approved, map your framework to Annex A controls and your business context.
Step 2 — Identify Risks and Assets
Start your risk identification by inventorying assets, listing every asset that supports business operations: data, applications, infrastructure, documentation, and even people with specialized knowledge. For each asset, evaluate its relationship to confidentiality, integrity, and availability.
For example, customer payment data requires high confidentiality, high integrity, and high availability, while internal meeting notes may require low confidentiality and availability but high integrity.
You can take an asset-based or process-based approach.
- Asset-based methodology catalogs everything of value and identifies threats against each item.
- Process-based methodology examines business workflows and identifies risks that could disrupt them.
Many organizations use both asset-based for IT infrastructure and data, and process-based for business operations. For each asset, map potential threats and vulnerabilities.
Threats: External forces that could cause harm
- Cybercriminals
- Natural disasters
- Human error
- System failures
Vulnerabilities: Weaknesses that threats can exploit
- Missing patches
- Weak passwords
- Inadequate backup procedures
- Untrained staff
Step 3 — Analyze and Evaluate Risks
Next, assign numerical values to each risk based on likelihood and impact. For example, you may calculate a very high probability (5) combined with a very high impact (5) as a risk score of 25 — your highest priority. A low likelihood (2) with medium implications (3) leads to a score of 6 — something to monitor but not necessarily treat immediately.
Your analysis criteria should account for different impact types. Financial impact matters, but so do reputational damage, regulatory penalties, operational disruption, and safety concerns. Consider that a data breach may cost just $50,000 in immediate response, but $500,000 in lost customer trust.
To evaluate, compare your risk scores against your risk appetite. Draw a line: risks above the threshold require treatment, while you can accept risks that fall below it. And don’t forget residual risk. After you apply controls, some risk always remains. Residual risk is typically calculated by re-evaluating likelihood and/or impact after controls are applied, using the same scoring method. Your residual risk must fall within acceptable limits, or you’ll need additional controls.
Step 4 — Select Risk Treatment Options
ISO 27001 defines four risk treatment options:
Avoid: Eliminate the risk by removing the activity or asset. For example, if you’re concerned about cloud storage security risks, you can mitigate them by keeping all data on-premises. Understandably, avoidance is rarely practical for core business functions.
Modify/Treat: Implement controls that reduce risk likelihood or impact to acceptable levels. For instance, installing endpoint detection and response tools reduces the risk of malware infections. Encrypting data at rest modifies the impact of a potential breach. Most risks fall into this category.
Share/Transfer: Pass the risk to a third party through insurance, outsourcing, or contracts. Cyber insurance transfers financial risk. Using a managed cybersecurity service provider transfers operational security risk. You remain accountable for the risk, but someone else shares the burden.
Retain/Accept: Consciously accept risks within your appetite or where treatment costs exceed potential impact. Document accepted risks explicitly. Auditors need to see that you made an informed decision, not an oversight.
Your Risk Treatment Plan (RTP) documents the selected treatment for each risk. It includes the specific controls you’ll implement, implementation timelines, responsible parties, and expected outcomes. The Statement of Applicability (SoA) links your RTP to Annex A controls, showing which of the 93 controls you’re implementing and why.
Step 5 — Monitor, Review, and Improve
Because business constantly changes, new threats emerge, and technology evolves, risk assessment isn’t an annual exercise but a continuous cycle. To keep your assessments current and relevant, establish a monitoring cadence that fits with your organizational context and risk appetite:
- Quarterly: Review high-priority risks
- Annually (or when significant changes occur, e.g., new systems, regulatory updates, security incidents): Conduct a complete risk assessment
- Ongoing: Monitor security metrics that indicate whether your controls are working as intended
Internal audits test your risk management process. Auditors verify that you’re following your documented procedures, that risk owners monitor assigned risks, and that treatment plans are progressing. Management reviews, required by clause 9.3, give leadership visibility into the risk landscape and ensure adequate resources support risk treatment efforts.
Clause 10 of ISO 27001 requires continual improvement. Each review cycle should make your risk assessment more accurate, your controls more effective, and your organization more resilient.
ISO 27001 Risk Management Framework Explained
A risk management framework integrates risk assessment into your broader ISMS. Think of it as the operating system that runs your security program. It defines how risk information flows through your organization, who makes decisions, and how those decisions translate into action.
- ISO 27001 clause 6.1 establishes risk management requirements.
- Clause 8.1 requires you to plan and control processes needed to meet information security requirements.
- Clause 9.3 demands management review of the ISMS, including risk assessment results.
These clauses work together to create an ongoing risk management cycle.
The framework aligns with ISO 27005 (information security risk management) and ISO 31000 (enterprise risk management) principles. You don’t need to implement these standards separately, but they provide useful methodology details that complement ISO 27001’s requirements.
The CIA triad (confidentiality, integrity, and availability) forms the foundation of your framework. Every risk ultimately threatens one or more of these properties.
Risk ownership and governance determine how decisions get made. Your framework should define:
- Who identifies risks (often security teams, but business units should contribute)
- Who analyzes and evaluates risks (usually a cross-functional risk committee)
- Who approves treatment decisions (typically executives for high-priority risks, managers for moderate risks)
- Who monitors ongoing effectiveness (risk owners with oversight from security leadership)
Clear governance prevents risks from falling through the cracks and ensures accountability throughout the process.
ISO 27001 Risk Assessment Template (Free Example)
A well-structured risk register makes assessment manageable. The WISE Risk Management Template, developed by the Risk Assessment Working group, provides a practical framework for documenting your risk assessment. Initially designed for e-infrastructures, the template adapts well to organizations of any size implementing ISO 27001.
The template uses a collaborative approach based on best practices from multiple organizations. It includes instructions that guide you through the assessment process and provides a structured format that aligns with ISO 27001:2022’s control categories.
Your risk register should capture these key fields:
- Asset: The information asset at risk (customer database, email system, employee records)
- Asset owner: The person responsible for the asset
- Threat: The potential danger (ransomware, insider threat, natural disaster)
- Vulnerability: The weakness that enables the threat (unpatched software, weak access controls)
- Existing controls: Security measures already in place
- Likelihood: Probability the threat will exploit the vulnerability (1-5 scale)
- Impact: Consequences if the risk materializes (1-5 scale)
- Risk score: Likelihood × Impact
- Risk level: Red/yellow/green based on your appetite
- Treatment option: Avoid, modify, share, or accept
- Planned controls: Additional security measures you’ll implement
- Residual risk: Expected risk level after treatment
- Risk owner: Person accountable for monitoring and treatment
- Status: Open, in progress, or closed
The WISE template uses a CC-BY license, making it freely available for organizational use. You can download and customize it to match your risk criteria and organizational structure. If you’re just starting your ISO 27001 journey, this template provides a proven foundation that reduces the learning curve significantly.
ISO 27001 Risk Assessment Examples
The following illustrative scenarios demonstrate how organizations approach risk assessment. While based on common industry patterns, these represent composite situations designed to show the risk assessment process in action across healthcare, finance, and small business contexts.
Scenario 1: Healthcare — Electronic Health Records (EHR) system breach
Consider a medical practice that identifies its EHR system as a critical asset requiring maximum confidentiality and integrity. The threat of ransomware, combined with vulnerabilities including legacy systems and limited IT staff, creates significant risk.
- Asset: Patient health records (10,000+ patients)
- Threat: Ransomware attack
- Vulnerability: Unpatched EHR software, limited endpoint protection
- Existing controls: Basic antivirus, weekly backups
- Initial risk: Likelihood (4) × Impact (5) = 20 (High/Red)
- Treatment: Implement endpoint detection and response, establish offline backup rotation, and conduct security awareness training
- Residual risk: Likelihood (2) × Impact (5) = 10 (Medium/Yellow)
- Applicable controls: A.8.7 (protection against malware), A.8.13 (information backup), A.6.8 (management of technical vulnerabilities)
In this scenario, the practice accepts the residual risk after treatment, documenting that complete elimination would require EHR replacement costing $200,000, disproportionate to the remaining risk level.
Scenario 2: Finance — Wire transfer fraud
A regional credit union faces business email compromise threats targeting its wire transfer processes. The vulnerability stems from email-based approval workflows without multi-factor verification.
- Asset: Wire transfer authorization system
- Threat: Business email compromise and social engineering
- Vulnerability: Email-only verification, no out-of-band confirmation
- Existing controls: Email security gateway, password policies
- Initial risk: Likelihood (4) × Impact (5) = 20 (High/Red)
- Treatment: Implement callback verification for all wire transfers over $10,000, require multi-factor authentication for financial system access, and establish transaction limits
- Residual risk: Likelihood (2) × Impact (4) = 8 (Low/Yellow)
- Applicable controls: A.5.16 (identity management), A.5.17 (authentication information), A.6.8 (management of technical vulnerabilities)
In this example, the credit union may also purchase cyber insurance to transfer residual financial risk, adding a layer of protection beyond technical controls.
Scenario 3: Small Business — Physical security and data theft
A 15-person consulting firm works with client data stored on laptops and a small office server. Physical security risks include after-hours office access and mobile device loss.
- Asset: Client project files and proprietary methodologies
- Threat: Physical theft of devices or unauthorized office access
- Vulnerability: No full-disk encryption, weak physical access controls, and no device tracking
- Existing controls: Office door locks, password-protected devices
- Initial risk: Likelihood (3) × Impact (4) = 12 (Medium/Yellow)
- Treatment: Deploy full-disk encryption on all devices, implement badge-based office access, enable device tracking and remote wipe capability, and establish a clear desk policy
- Residual risk: Likelihood (2) × Impact (3) = 6 (Low/Green)
- Applicable controls: A.7.7 (clear desk and clear screen), A.7.8 (equipment siting and protection), A.8.4 (physical media handling)
In this scenario, the firm accepts the residual risk, noting that insurance covers device replacement costs and encryption protects data confidentiality even if a device is stolen.
Scenario 4: Healthcare — Insider threat to patient privacy
A hospital system identifies risks when employees access patient records without a business need, a common scenario for HIPAA violations.
- Asset: Electronic medical records system
- Threat: Unauthorized access by employees (curiosity, fraud, or harassment)
- Vulnerability: Overly broad access permissions, limited audit logging
- Existing controls: Role-based access control, annual compliance training
- Initial risk: Likelihood (3) × Impact (5) = 15 (High/Red)
- Treatment: Implement the principle of least privilege access review, deploy user behavior analytics to flag unusual access patterns, establish a monthly audit log review process, and require justification documentation for sensitive record access
- Residual risk: Likelihood (1) × Impact (5) = 5 (Low/Green)
- Applicable controls: A.5.15 (access control), A.5.16 (identity management), A.8.15 (logging)
The hospital maintains the monitoring program indefinitely, recognizing that insider threats require ongoing vigilance rather than one-time fixes.
ISO 27001 Standards and Related Guidance
ISO 27001:2022 defines risk assessment requirements across several clauses.
- Clause 6.1.2 specifically addresses information security risk assessment, requiring organizations to identify confidentiality, integrity, and availability risks.
- Clause 6.1.3 covers information security risk treatment, mandating that you select and implement appropriate risk treatment options.
- Clause 8.2 ties risk assessment to control implementation by requiring that your risk treatment plan determine which controls you deploy.
Annex A underwent significant restructuring in the 2022 revision. The standard now organizes 93 controls across four themes:
- Organizational controls (37 controls): Policies, roles, risk management, supplier relationships
- People controls (8 controls): Screening, training, disciplinary process
- Physical controls (14 controls): Secure areas, equipment protection, disposal
- Technological controls (34 controls): Access control, cryptography, logging, network security
Your risk assessment determines which of these 93 controls apply to your organization. You don’t need to implement all controls, just those that address your identified risks.
ISO 27005:2022 provides detailed risk management guidance that complements ISO 27001. Where ISO 27001 tells you what to do, ISO 27005 shows you how. The standard expands on risk assessment methodologies, offers examples of risk scenarios, and provides guidance on selecting appropriate controls.
ISO 31000:2018 offers enterprise risk management principles applicable beyond information security. Organizations implementing ISO 27001 and broader ERM programs use ISO 31000 to create a consistent risk language and methodology across the enterprise.
ISO 31010:2019 focuses specifically on risk assessment techniques. It catalogs dozens of approaches — from simple brainstorming to complex quantitative modeling — helping you select methods appropriate to your organization’s size and complexity. This control supports ISO 31000 by providing methods such as checklists, FTA, and Monte Carlo analysis.
You don’t need to purchase and implement all these standards; ISO 27001 contains everything required for certification. The related standards provide additional depth for organizations wanting to refine their approach or integrate information security risk management with broader enterprise risk programs.
How to Simplify the Process
Organizations often overcomplicate risk assessment by building elaborate spreadsheets with dozens of fields, attempting to assess every conceivable risk, which creates burdensome processes that no one follows. The reality is that simplicity wins.
Manual vs. Automated Approaches
Spreadsheet-based risk assessment works for small organizations. The advantages:
- Low cost, with complete control over structure
- No learning curve — everyone understands spreadsheets
- Quick to set up using templates like WISE
But the disadvantages of a manual approach emerge as your business grows:
- Don’t scale well past 100-200 risks
- Version control becomes problematic with multiple users
- Difficult to generate reports for management or auditors
- Hard to track changes over time and maintain audit trails
GRC platforms automate much of the process with templates aligned with ISO 27001, automated risk scoring, workflow management, and built-in reporting. Users collaborate in real-time, and the system maintains a complete history of changes.
The tradeoff is cost and complexity. GRC platforms require a budget for licensing and implementation. Smaller organizations often find spreadsheets sufficient until they reach 50+ employees or begin managing multiple compliance frameworks simultaneously.
Common Mistakes to Avoid
Organizations preparing for ISO 27001 certification often make predictable mistakes:
- Too broad or too narrow: Some organizations identify only 10-15 risks at a high level (like “cybersecurity threats”). Others identify 500+ granular risks, creating unmanageable overhead. Aim for 50-150 risks that balance specificity with manageability.
- Inconsistent scoring: Different people applying your risk criteria reach different conclusions. Avoid this by providing detailed examples in your framework documentation and calibrating scores across risk assessors.
- Neglecting residual risk: Organizations document initial risk but forget to calculate residual risk after treatment. Auditors need to see that your controls reduce risk to acceptable levels.
- Missing linkages: Clearly link your Statement of Applicability (SoA) to your risk assessment. Auditors will ask, “Why did you implement this control?” The answer should trace directly to a risk in your register.
- Static assessments: Treating risk assessment as an annual compliance exercise rather than a living process. Your risk register should change throughout the year as new threats emerge and business conditions evolve.
Audit Preparation Tips
Certification auditors examine your risk assessment closely. Make their job easier by:
- Ensuring every Annex A control in your SoA links to a specific risk
- Documenting your risk criteria clearly, including how you define likelihood and impact levels
- Showing evidence that management approved your risk framework and reviewed the results
- Demonstrating that risk owners actively monitor their assigned risks
- Maintaining a clear audit trail of risk assessment updates and rationale for treatment decisions
Xantrion helps organizations navigate ISO 27001 certification by streamlining the risk assessment process. Our approach combines proven templates with expert guidance, helping you build a risk management framework that satisfies auditors while remaining practical for daily use. Want to learn more? Get in touch today.
Key Takeaways
ISO 27001 risk assessment follows a structured five-step process: define your framework, identify risks and assets, assess likelihood and impact, select treatment options, and monitor continuously. Each step builds on the previous, creating a comprehensive view of your information security.
The process isn’t just about compliance. Organizations that take risk assessment seriously make better security decisions, allocate resources more effectively, and respond faster when threats emerge. And certification requires evidence that you’re consistently following your documented approach. Auditors want to see clear linkages between identified risks, selected controls, and business context.
Whether starting your ISO 27001 journey or refining an existing program, remember that effective risk assessment balances thoroughness with practicality. Use proven templates like the WISE Risk Management Template to avoid reinventing the wheel. Focus on risks that matter to your organization rather than trying to address every theoretical scenario.
Ready to simplify your ISO 27001 risk assessment process? Xantrion’s security experts help organizations build practical risk management frameworks that satisfy certification requirements without overwhelming your team. Learn how our team can simplify ISO 27001 certification for your organization.

