Every data breach starts the same way: “We thought we were secure.” The difference between organizations that quickly recover and those that don’t often comes down to whether they had robust cybersecurity compliance programs in place before disaster struck.
Compliance isn’t only about avoiding fines or passing audits. It’s about building a security approach that effectively stops attackers and demonstrates to customers, partners, and regulators that you’re serious about protection.
Let’s take a closer look at cybersecurity compliance: which frameworks apply to your business, how to implement them without breaking your budget, and why getting started now is better than waiting for regulators to come knocking.
What Is Cybersecurity Compliance?
Achieving cybersecurity compliance involves adhering to the security rules that apply to your business. Think of it as the minimum security controls required to protect data, systems, and operations, as mandated by various authorities.
Cybersecurity compliance definition
Regulators and standards bodies establish cybersecurity compliance requirements based on identified threats and proven security practices. Achieving compliance requires your organization to implement specific cybersecurity measures, document its processes, and demonstrate that it follows them.
What happens if you don’t comply? Legal regulations are enforceable, and agencies can fine you, shut down your operations, or pursue criminal charges for violations. Although typically voluntary, industry standards often become mandatory due to contractual or customer requirements.
Scope of compliance (laws, standards, internal policies)
Compliance frameworks target the CIA triad — confidentiality, integrity, and availability.
- Confidentiality protects sensitive data from unauthorized access.
- Integrity ensures information stays accurate and unchanged.
- Availability keeps systems running when people need them.
Cybersecurity vs compliance in practice
Security and compliance have significant overlap, but they aren’t identical. Compliance establishes the baseline and outlines the minimum controls your organization must implement. Security encompasses everything you do to protect your organization against cybersecurity risks, which often goes beyond compliance requirements.
The most effective compliance programs include three key components. These include written policies that define security requirements, regular risk assessments that identify threats and vulnerabilities, and technical controls that enforce security measures. Documentation proves you follow your policies, and regular testing verifies your controls work as intended.
Why Cybersecurity Compliance Matters
Strong cyber security and compliance programs provide tangible business benefits beyond simply meeting regulatory requirements.
Protecting sensitive data and privacy
Data breaches cost organizations an average of $4.4 million per incident; however, the damage often extends beyond immediate financial losses. Customer trust erodes, competitive advantages disappear, and rebuilding takes years.
Compliance frameworks address data protection through access controls, encryption requirements, and privacy safeguards. For example, GDPR’s data minimization principle reduces breach exposure by limiting the personal data collected and retained. At the same time, HIPAA’s safeguards protect patient information that could lead to identity theft or discrimination if it were to be exposed.
Reducing risk and avoiding penalties
Regulatory penalties often grab headlines, but they typically constitute the smallest part of the overall financial impact. GDPR fines can reach 4% of global annual revenue, while HIPAA violations range from $100 to $50,000 per affected record. Non-compliance with PCI DSS can result in monthly fines and increased transaction fees.
Compliance violations also trigger additional costs: legal fees, forensic investigations, credit monitoring for affected individuals, and increased cybersecurity insurance premiums. Additionally, regulators can require an organization to halt operations until it fixes compliance issues.
Building trust and reputation
Compliance certifications signal to customers, partners, and investors that you take security seriously. When two consulting companies bid for the same project, the one with documented security practices and third-party attestations usually wins.
If (or when) a cyber incident occurs, compliance can make a positive difference. Organizations with strong compliance programs can demonstrate to customers, regulators, and the media that they have appropriate controls and have followed proper incident response procedures. By comparison, organizations without compliance programs look negligent.
Key Cybersecurity Compliance Standards & Frameworks
Different industries and jurisdictions have developed various compliance requirements. To build an effective compliance program, you must first understand which cybersecurity compliance and data protection standards apply to your organization.
Global standards
GDPR
The General Data Protection Regulation applies to any organization that processes personal data of EU residents, regardless of the organization’s physical location. GDPR requires explicit consent for data collection, grants individuals the right to access and delete their data, and mandates breach notification within 72 hours.
ISO/IEC 27001
ISO 27001 provides a comprehensive framework for cybersecurity compliance and information security management systems (ISMS). The standard requires organizations to establish security policies, conduct risk assessments, implement appropriate controls, and continuously monitor their security posture.
NIST CSF
The National Institute of Standards and Technology Cybersecurity Framework organizes security activities into six core functions: Identify, Protect, Detect, Respond, Recover, and Govern. Initially developed for critical infrastructure, NIST CSF has become widely adopted across industries for cybersecurity regulatory compliance.
Industry-specific frameworks
HIPAA
The Health Insurance Portability and Accountability Act requires healthcare organizations to protect patient health information. HIPAA’s Security Rule mandates administrative, physical, and technical safeguards for electronic protected health information (ePHI).
PCI DSS
The Payment Card Industry Data Security Standard applies to any organization that stores, processes, or transmits payment card data. PCI DSS requires secure network configurations, regular vulnerability scanning, strong access controls, and continuous monitoring.
SOX
The Sarbanes-Oxley Act, also known as SOX, requires public companies to establish internal controls over financial reporting. While not specifically a cybersecurity regulation, SOX has significant IT implications because financial systems must have adequate security controls in place.
SOC 2
Service Organization Control 2 reports evaluate controls relevant to security, availability, processing integrity, confidentiality, and privacy.
FFIEC
The Federal Financial Institutions Examination Council provides cybersecurity guidance for banks, credit unions, and other financial institutions. FFIEC guidance covers risk assessment, board oversight, security controls, and incident response.
Government & defense regulations
FISMA
The Federal Information Security Modernization Act requires federal agencies and contractors to implement NIST-based security programs. FISMA compliance entails categorizing information systems, selecting suitable security controls, and conducting regular security assessments.
CMMC
The Cybersecurity Maturity Model Certification requires defense contractors to demonstrate cybersecurity maturity through third-party assessments.
DFARS
The Defense Federal Acquisition Regulation Supplement (DFARS) requirements mandate specific cybersecurity controls for defense contractors handling Controlled Unclassified Information (CUI).
Emerging & international frameworks
NIS2
The Network and Information Security Directive 2 expands cybersecurity requirements across critical infrastructure sectors in the EU.
DORA
The Digital Operational Resilience Act applies to financial services organizations operating in the EU.
Essential Eight
Australia’s Essential Eight provides prioritized cybersecurity strategies based on their effectiveness in preventing cyber incidents. The strategies include:
- Application control
- Patch applications
- Configure Microsoft Office macros
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Regular backups
Cyber Essentials
The UK’s Cyber Essentials scheme helps organizations demonstrate their adherence to basic cybersecurity controls.
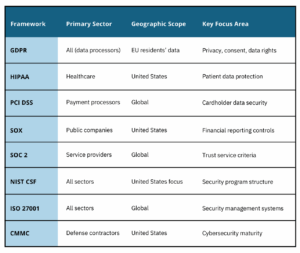
Comparison table: Which framework applies to you?
Steps to Achieve Cybersecurity Compliance
Building a cyber compliance program requires careful planning and execution. Most successful programs follow these key steps:
Assign a compliance owner/team
To increase your chances of success in cybersecurity compliance, ensure that someone within your organization is responsible for compliance. For example, smaller companies may assign compliance responsibilities to an existing IT or operations manager, while larger organizations often need dedicated compliance officers or teams.
The compliance owner should have a thorough understanding of your business operations and the relevant regulatory requirements that apply. They’ll coordinate between departments, manage vendor relationships, and ensure that compliance activities receive the appropriate resources and attention.
Conduct risk analysis & gap assessment
Begin by assessing your current security posture against the requirements of the cybersecurity compliance framework. Perform a risk assessment to identify assets, threats, vulnerabilities, and potential impacts.
Additionally, perform a gap assessment to compare existing controls to regulatory requirements. Focus your gap assessment on requirements with the highest risk or compliance impact. You don’t need to fix everything immediately, but you should prioritize issues that could result in significant penalties or business disruption.
Implement technical and administrative controls
Compliance frameworks typically require both technical (such as firewalls, encryption, and access management) and administrative controls (policies, procedures, and training). Technical controls often receive the most attention, but administrative controls frequently lead to compliance failures.
Start with foundational controls that support multiple compliance requirements. For example, multi-factor authentication strengthens access controls across most frameworks, while regular vulnerability scanning supports PCI DSS, FISMA, and many other standards.
Establish policies, training, and awareness programs
Create written policies that are specific enough to guide employee behavior but flexible enough to accommodate business changes.
Provide employee training to ensure everyone understands their compliance responsibilities. Remember, different roles need different training — executives need strategic awareness, while system administrators need technical details. Offering regular training updates and security awareness programs to help employees learn how to spot and report potential incidents.
Monitor, audit, and document compliance continuously
Compliance requires ongoing monitoring, assessment, and improvement, and auditors and regulators want you to demonstrate compliance through thorough documentation. Keep records of policy updates, training completion, vulnerability remediation, and incident response activities. Consider implementing an electronic documentation system, which makes it easier to track and retrieve compliance evidence.
Quick-start compliance checklist
- Identify applicable compliance requirements
- Assign compliance ownership and responsibilities
- Conduct an initial risk and gap assessment
- Develop a compliance project plan with timelines
- Implement foundational security controls
- Create and approve required policies
- Establish employee training programs
- Set up compliance monitoring and documentation systems
- Schedule regular internal assessments
- Plan for external audits or certifications
Common Challenges and How to Overcome Them
Regardless of their size or industry, the reality is that most organizations face similar cybersecurity compliance challenges. Understanding these obstacles helps you prepare and develop mitigation strategies.
Overlapping regulations & complexity
Organizations often must meet multiple compliance requirements that seem to conflict or duplicate each other. Different regulations use different terminology for similar concepts, making it hard to understand how requirements relate. For example, a healthcare technology company may need to simultaneously meet HIPAA, SOC 2, GDPR, and state privacy laws.
Limited budget and resources
Cybersecurity compliance programs compete with other business priorities for funding and attention. Small organizations often lack dedicated security staff, while larger companies struggle to find qualified compliance professionals.
Compliance costs include:
- Technology purchases
- Staff time
- External consulting
- Audit fees
- Opportunity costs from time spent on compliance instead of other activities
- Ongoing maintenance costs
Vendor and supply chain risks
When it comes to compliance, the fact remains: Your organization is only as compliant as your least secure vendor. You’re responsible for compliance violations even if a third-party vendor causes the problems. When you give vendors access to your sensitive data and systems, you’re still on the hook if something goes wrong. If a vendor gets breached and your customer data is exposed, regulators hold you accountable, not the vendor.
Keeping up with evolving threats & frequent updates
Compliance requirements are subject to frequent changes as new threats emerge and regulations evolve. Framework updates, regulatory guidance changes, and new legal interpretations can render existing compliance efforts invalid.
Technology changes also affect compliance requirements. Cloud computing, remote work, and mobile devices create new security challenges that existing regulations didn’t anticipate. Your organization must constantly adapt its compliance programs to address these ever-changing risks.
Practical solutions
Thankfully, numerous strategies can help your organization overcome these common cybersecurity compliance challenges without breaking the bank — or overwhelming your internal resources:
- Automation reduces compliance costs and improves consistency. By automating vulnerability scanning, log analysis, and policy enforcement, your organization can maintain compliance with less manual effort. Configuration management tools ensure systems maintain compliant settings over time.
- Risk-based prioritization enables organizations to focus their limited resources on the most critical compliance activities. Not every requirement deserves equal attention; focus on controls that address your highest risks and most severe potential impacts.
- Compliance partners can provide expertise and capabilities that organizations lack internally. For example, a managed security service provider like Xantrion can handle ongoing monitoring and maintenance, while compliance consultants help with assessments and program development. External auditors provide independent validation that your program works as intended.
Cybersecurity Compliance Trends and Updates
Several trends are shaping the cybersecurity regulatory compliance environment for the coming years.
SEC disclosure rules for public companies
The Securities and Exchange Commission now requires public companies to disclose material cybersecurity incidents within four business days and provide annual reports on cybersecurity risk management and governance. These rules treat cybersecurity incidents like other material business risks that could affect investor decisions.
Rise of state-level and regional privacy laws
Following California’s Consumer Privacy Act (CCPA) and its expansion through the California Privacy Rights Act (CPRA), other states have enacted comprehensive privacy legislation. Virginia’s Consumer Data Protection Act (VCDPA) and similar laws in Colorado, Connecticut, and other states create a patchwork of privacy requirements. Organizations operating in multiple states must navigate different requirements for data subject rights, consent mechanisms, and breach notification timelines.
International tightening of regulations
As we’ve already pointed out, the European Union’s NIS2 directive expands cybersecurity compliance obligations beyond critical infrastructure. The Digital Operational Resilience Act (DORA) creates comprehensive ICT risk management requirements for financial services. The UK’s Telecoms Security Act requires telecommunications providers to assess network security risks and gives regulators authority to restrict high-risk vendors from critical network functions. The trend continues; other countries are developing similar comprehensive cybersecurity legislation.
AI and automation in compliance monitoring
Artificial intelligence and machine learning help organizations monitor compliance more effectively and efficiently. But using AI in compliance monitoring raises new concerns about algorithmic bias, explainability, and regulatory acceptance. You must ensure that your AI-driven compliance decisions can be explained and justified to auditors and regulators.
Conclusion: Building Security Through Compliance
Cybersecurity compliance offers a structured approach to developing and enhancing organizational security capabilities. While compliance alone doesn’t guarantee perfect security, it establishes proven controls and processes that significantly reduce risk.
Threats evolve, regulations change, and business requirements shift over time, meaning compliance is an ongoing process rather than a destination. Take the time to honestly assess your current compliance status. Which regulations apply to your organization? What controls do you already have in place? Where are the biggest gaps between your current security posture and compliance requirements?
Building an effective cybersecurity compliance program requires significant expertise and ongoing attention to detail. Many organizations find that partnering with an experienced cybersecurity services provider like Xantrion helps them achieve compliance faster while reducing internal resource demands.
Whether you build compliance capabilities internally or work with external partners, the key is to get started with a clear plan and realistic timelines. Your future self (and your customers) will thank you for taking action today rather than waiting for a breach to force your hand.
Frequently Asked Questions
What happens if you’re not compliant?
Consequences of non-compliance vary depending on the specific regulation and its level of severity. Penalties can include financial fines, restrictions on business operations, increased regulatory oversight, and even civil or criminal liability for executives.
Beyond direct penalties, non-compliance often triggers indirect costs, such as increased insurance premiums, customer contract losses, and competitive disadvantages. Regulatory investigations can consume significant management time and legal expenses, even when they don’t result in formal penalties.
Who is responsible for compliance in a company?
Compliance responsibility ultimately rests with executive leadership and the board of directors, but day-to-day compliance management typically involves multiple roles. For example, at larger organizations, Chief Information Security Officers (CISOs) often oversee technical compliance requirements, while legal teams are responsible for interpreting and reporting on regulations. And smaller organizations may assign compliance responsibilities to existing IT managers or operations staff.
Does compliance guarantee security?
No. Compliance establishes minimum security baselines but doesn’t guarantee complete protection against all threats. Think of compliance as a tool in your cybersecurity toolkit. It’s a good start, not a total defense. Your compliance framework can provide a solid foundation, but your organization must implement additional security measures tailored to its specific risks and threat environments.
How often should compliance audits happen?
That depends on several factors, including regulatory requirements, business risk tolerance, and organizational changes. Many frameworks require annual external audits, while others specify continuous monitoring or periodic self-assessments.
Does cybersecurity compliance apply to small businesses?
Many compliance requirements apply regardless of organizational size, though some regulations have small business exemptions or reduced requirements. GDPR applies to any organization that processes EU resident data, while PCI DSS requirements vary based on the organization’s transaction volume.
It’s worth noting that small businesses often face the same threats as larger organizations, but have fewer resources to address them. Compliance frameworks can give your small business a structured approach to implementing essential security controls within your budget constraints.
What’s the difference between compliance and cybersecurity best practices?
Compliance focuses on meeting minimum regulatory requirements, whereas cybersecurity best practices encompass all activities that enhance an organization’s security posture. Best practices often exceed compliance requirements and address emerging threats that regulations haven’t yet incorporated.
Do small or midsize businesses need a dedicated compliance officer?
Dedicated compliance officers are beneficial for organizations with complex regulatory requirements or a high compliance risk. But many small and midsize businesses successfully manage compliance responsibilities within existing roles. The key is to ensure that someone has clear accountability for compliance oversight, adequate time to fulfill their responsibilities, and access to the necessary expertise through training or external resources.
Know your organization needs compliance help, but can’t afford a dedicated compliance officer? In that case, a managed security service provider like Xantrion can assist. Our turnkey cybersecurity and compliance services help you identify, detect, protect, and respond to threats, proving due diligence and ensuring you’re audit-ready. Get in touch today.

