Since uncertainty still surrounds the Securities and Exchange Commission’s pending cyber risk management rules for registered investment advisers, Xantrion CTO, Christian Kelly, attended the recent 2024 Investment Adviser Compliance Conference, which included remarks from SEC officials. Unfortunately, those officials were limited in how much they could share since the rules have yet to be finalized. The uncertainty notwithstanding, what is…
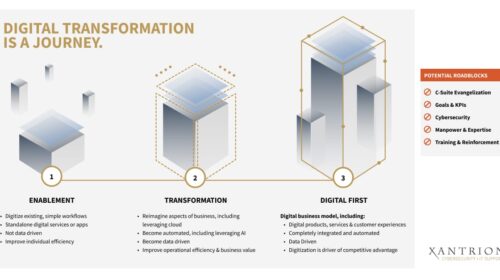
By Mike Rose, CEO, Engine Room, Christian Kelly, CTO, Xantrion, and Seth Tuman, COO, 2Go Advisory Group For growing businesses, digital transformation is exciting, necessary…and sometimes challenging to understand. One way to imagine your digital transformation journey is to consider it in three stages: enablement, transformation and digital first. The infographic below, created by experts from Engine Room, Xantrion and…
With increased regulatory pressure and mounting cybersecurity risks, it’s more important than ever to make sure you’ve got a robust cybersecurity program. This checklist will help you shape your 2024 cybersecurity strategy. DOWNLOAD INFOGRAPHIC Get a Free Cyber Risk Assessment
Here at Xantrion, we’ve been experimenting with different AI-powered tools and automation for the last three years. As a mid-size managed IT service provider, we’ve learned a lot about the potential and the limitations of AI tools, and what they mean for businesses like ours…and yours.
The concept of digital transformation actually predates AI and machine learning. As you update and evolve your business’s use of technology, it’s important to understand all three concepts.
There’s aspect of the battle against cyber criminals that organizations can’t afford to ignore: Employee morale and company culture. While strong morale and culture can help companies protect against cyberthreats, weak morale and culture can make them more vulnerable.
When your business evolves from a scrappy startup to a more mature organization, there’s a good chance that your managed service provider (MSP) won’t evolve with it. Solo IT consultants or AI-based MSPs may work well for fledgling businesses, but as a company grows, so does its IT needs…meaning its old MSP may no longer be the right fit. If…
It’s any business leader’s worst nightmare: A cyberattack that paralyzes their entire company, from top to bottom, leading to work stoppages, delivery delays, and devastatingly high costs. Over the years, Xantrion has been called multiple times to help different companies reeling from cyberattacks. Each time, Xantrion has helped them get back on their feet. In the interview below, Xantrion Chief…
Gaps in cybersecurity recently cost MGM Resorts a reported $100 million after cybercriminals hacked the casino giant. Though disastrous for MGM, other companies can learn valuable lessons from the headline-making cyberattack…without paying $100 million to do so. Here are a few key takeaways from this incident: 1. Beware the power of social engineering. Social engineering is the criminal act of…
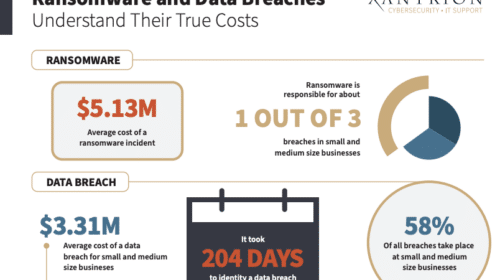
New data from IBM and Verizon shed light on the true costs of ransomware and data breaches. Do you understand the risks of leaving your business unprotected?
It might happen on a Friday afternoon, or maybe on the day before holiday. Many employees have clocked out early, so an intrusion goes unnoticed…until it’s too late. Suddenly the whole system begins shutting down. Your next step? Panic. A data breach or other cybersecurity incident can be a traumatic, shocking experience, even for a seasoned executive. To avoid freezing…
Staying vigilant about cybersecurity threats is a requirement for doing business today. The costs of data breaches are climbing sky-high, while AI is empowering criminals to devise ever more sophisticated schemes to steal from and defraud companies. That’s why businesses turn to IT security providers who offer services and expertise that their in-house IT teams lack. But not all security…
There’s a good chance your company’s internal IT team is feeling overwhelmed. It’s not a reflection of their skill or dedication, but rather a sign of the times — technology and cybersecurity threats are evolving faster than ever. Sometimes companies are victims of their own success: They’re growing so quickly that their in-house IT departments can’t keep up with requests…
By Adrian Bray, CEO, Stellar Consulting in partnership with Xantrion Management often has a love-hate relationship with technology. While it is a part of their daily life, they typically only interact with the IT department during onboarding, offboarding, or when there is a problem. In addition, IT-related costs are increasingly a more significant portion of the P&L. IT and digital…
Years ago, when businesses needed tech support beyond what they could manage in-house, they often turned to IT consultants. But as the technology landscape grew more complex and security threats spiked, companies needed more than ad hoc consulting services — they sought to fully outsource their technology function. Enter managed service providers, or MSPs. What is an MSP? In basic…
The COVID-19 pandemic changed the way we work primarily by accelerating the widespread adoption of remote work. As pandemic safety measures eased, many companies had hoped to bring employees back into the office this year. However, the Wall Street Journal noted in May that most efforts pushing for a return to fully on-premise work had stalled. In fact, nearly 60%…
Performance is top of mind for CFOs and COOs who are trying to do more with fewer resources. They are facing more pressure than ever to justify their spending and prove they’re providing value. Our goal is to help every department, not just IT, get what they want while still delivering results. The following are 9 ways we’ve found to get the best value from your IT investment.…
By Chris Valiquet, Senior Salesforce Consultant, StarrData In a recent blog post, we explored how we plan to begin implementing Artificial Intelligence (AI) technologies to enhance our business practices at Xantrion and why we feel it’s important for our clients to start thinking about how to leverage AI-based technologies. While many solution providers are beginning to tap into the possibilities of…
To keep your key systems functional, you need two centralized teams to oversee your entire network: a security operations center (SOC) and a network operations center (NOC). Your SOC monitors, responds to, and remediates security threats to protect applications and data against cyberattacks. Your NOC keeps an eye on network status, applies updates and patches, and provides tech support…
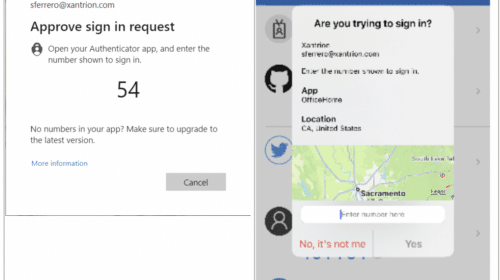
You have probably heard of some high-profile network breaches in the news in recent months. Threat actors targeting organizations both large and small and have found success breaching secure environments using a technique called MFA spamming. This is a highly effective tactic because it targets the person, not the technology, to work around an organization’s MFA protections. Companies as large…
When discussing the importance of adopting a strong cybersecurity strategy, too often the focus is on technology solutions designed to prevent and mitigate cyber-attacks. Certainly, the adoption of tools and solutions is integral to a strong security posture. Yet, as noted in Verizon’s 2022 Data Breach Investigations Report, a staggering 82 percent of data breaches involve some sort of human…
In recent years, cybersecurity has been a considerable concern for middle market companies. Threats are far more frequent, diverse, and severe than anyone could have anticipated. It’s crucial that all organizations implement cyberdefense measures that better safeguard company and customer information to mitigate financial losses and brand damage. From lingering threats related to the COVID-19 pandemic, to geopolitical conflicts and…
Organizations are always looking for ways to effectively manage costs, improve productivity, and scale efficiently. One method proven to help achieve these goals is to outsource IT support to a managed service provider (MSP). Not only is outsourcing typically 30-40% cheaper than hiring in-house1, it can also help you close critical gaps in your IT and cybersecurity infrastructure. Below are…
A good password is a critical part of protecting your data. So, when LastPass, a popular password manager solution, announced that its third-party cloud-based storage service had been breached, allowing an unknown attacker to gain access to backups containing customer data including password vaults, a lot of people got nervous. The bad news is that those customer password vaults are in…
According to a recent RSM report, 40% of midsized companies outsource IT services to obtain cost-effective expertise and keep current with rapidly changing technology and threats. The critical issue these companies face is determining which IT outsourcing company to trust, since the report also found that many mid-market companies are worried about a cyberattack on a supplier. As an industry…
Security remains one of the biggest concerns and most challenging responsibilities facing small and medium-sized businesses (SMBs) today. In 2021, there was a 300% increase in ransomware attacks with over 50% reaching small businesses. To address this challenge, Microsoft is investing in security solutions purposefully designed to help protect them. Microsoft Defender for Business is a new endpoint security solution…
By Robert Thomas, Audit Senior Manager, WithumSmith+Brown, PC and Christian Kelly, IT Auditor, Xantrion Inc. Congratulations! Your pharmaceutical, biologic, or medical device startup has developed a promising product, and you’re ready to raise a Series B round of funding. Read on to learn what experts Rob Thomas and Christian Kelly recommend to make it easier to pursue and obtain that…
Multi-factor authentication (MFA) is a great way to add an extra layer of security to network access. But it’s not foolproof – as Cisco, Microsoft, and Uber all learned recently when cybercriminals breached their network using a technique known as MFA spamming. Also known as MFA bombing and MFA fatigue, this ploy is used by an attacker who has acquired…
Phishing is when criminals use fake emails, social media posts or direct messages with the goal of luring you to click on a bad link or download a malicious attachment. If you click on a phishing link or file, you can hand over your personal information to the cybercriminals. A phishing scheme can also install malware onto your device. No need…
Last year’s headline-grabbing ransomware attacks on the Colonial Pipeline and meatpacking company JBS show how vital it is to remain vigilant in your efforts to protect yourself from ransomware. For several days, the attacks shut down one of the most vital oil pipelines in the US and disrupted the global meat supply chain. They also cost each company millions of…